Hack DNS for lightning-fast Web browsing
Posted On Saturday, January 19, 2008 at at 1/19/2008 02:49:00 AM by nullNo matter how big the broadband pipe you use to surf the Web, it's not big enough. Everyone, whether they use a slowpoke dial-up modem or the fastest FiOS line, wants to surf faster.
There's a simple way you can get to Web sites faster, and it won't cost you a penny. You can hack the way your PC uses the Domain Name System (DNS), the technology underlying all Web browsing. It's far simpler to do than you might imagine, as you'll see in this article.
Understanding DNS
Before you start, it's a good idea to get a basic understanding of how DNS works. When you type in a URL such as www.computerworld.com, that URL needs to be translated into a numeric IP address that Web servers and Internet routers can understand. When you type in a URL, a DNS server does the translation, from www.computerworld.com to 65.221.110.98, for example.
DNS servers live on the Internet, and your computer contacts them with the request to do that translation, which is commonly called name resolution. When you use an ISP, your computer will automatically use the default DNS servers specified by your ISP; you typically don't need to set up DNS in any way. If you're on a corporate network, your systems administrator may have set you up to use specific DNS servers.
If there's a delay in contacting the DNS server, or if the DNS server takes too much time resolving the address, you'll face a delay in getting to a Web site. So even if you've got the world's fattest pipe, your Web surfing will be slowed down.
If you could speed up the name resolution in some way, you'd be able to speed up your Web surfing. And that's exactly what I'll show you how to do.
Speed up Web browsing with OpenDNS
Here's the simplest way to hack DNS to speed up your Web browsing: Use free, superfast DNS servers run by the OpenDNS service instead of your ISP's DNS servers. OpenDNS has a monstrously big DNS cache, with DNS servers around the world, so you'll be able to retrieve IP addresses from it more quickly than from your ISP's DNS servers.
As I'll explain a little later in this article, the service includes other benefits as well, such as letting you create browser shortcuts so that you could go to www.computerworld.com, for example, by just typing the letter c in your browser and pressing Enter.
The addresses of the OpenDNS servers are 208.67.222.222 for a primary DNS server and 208.67.220.220 for a secondary server.
To use the OpenDNS servers, you'll have to tell your computer to use them. If you have Windows XP, first select Control Panel --> Network and Internet Connections --> Network Connections, right-click your network connection from the Network Connections window, and select Properties. A dialog box like that shown below appears.
 | |
| Highlight the Internet Protocol (TCP/IP) listing and select Properties in order to get to a dialog box that will let you use OpenDNS server. (Click image to see larger view.) |
Scroll down to the Internet Protocol (TCP/IP) listing and select Properties. At the bottom of the screen, select "Use the following DNS server addresses." For the Preferred DNS server, enter this address: 208.67.222.222. For the Alternative DNS server, enter this address: 208.67.220.220. Click OK, and then click Close and Close again. Restart your PC in order for the settings to take effect. The figure below shows the screen filled out properly.

| Telling your PC to use the OpenDNS servers. (Click image to see larger view.) |
If you're using Windows Vista, select Control Panel --> Network and Internet --> Network and Sharing Center. Click the View Status link on the right side of the screen. The Local Connection Status screen appears, as shown in the figure below. Click Properties.

| Click Properties in order to get to a dialog box that will let you use OpenDNS servers. (Click image to see larger view.) |
You'll come to the same dialog box as you would for XP that lets you use the OpenDNS servers. Follow the same directions as for using OpenDNS on XP, and you'll be set.
When you configure a PC to use OpenDNS, only that PC will be able to use the OpenDNS servers. If you want all of the PCs on your network to use the servers, you can tell your router to use the OpenDNS servers, and then all of your PCs on the network will follow suit. That way, you won't have to configure each individual PC.
The way you do this will vary from router to router, and it changes according to whether you're using a router for a home office/small office or a larger corporate router. For a small office/home office router, you'll log into your router, look for the DNS settings, and then use the OpenDNS settings of 208.67.222.222 for the primary DNS server and 208.67.220.220 for the alternative DNS server.
Whether you run a small network or larger network, you can get benefits beyond faster DNS. The service also gives you DNS management tools such as domain blocking. It also gives you statistics and charts about your network's DNS use.
On Linksys SRX 400 and many other Linksys routers, log into your router by going to the log-in page at 192.1681.1, using admin as the password and leaving the username blank. Scroll down the page until you come to the Static DNS 1 and Static DNS 2, as shown in the figure below. Click Save Settings. Restart your router and the PCs on your network, and they will begin using the OpenDNS DNS servers.

| Change the DNS settings on this screen to use the OpenDNS servers for your entire network. (Click image to see larger view.) |
If you run a corporate network and need help getting it set up, your best bet is to go to the OpenDNS FAQ page.
Note that OpenDNS may not work when using a virtual private network. For example, I wasn't able to get it to work using a Cisco VPN. And if you're on a corporate network, you should check with your systems administrator before using OpenDNS.
OpenDNS also lets you create shortcuts that let you visit Web sites by typing in a letter or group of letters instead of a full URL. To do that, you'll first need to register, which is free. After you do that, go to the site, log in, and click the Shortcuts link. On the page that appears, type in the shortcut text in the top box, and the URL in the bottom box and click Create Shortcut. From now on, when you type the shortcut text into your browser window, you'll be sent to the full URL.
You can also add the OpenDNS bookmarklet (found at the bottom of the page) to your browser and, in that way, create a shortcut no matter where you are on the Internet.

| Creating a shortcut in OpenDNS. (Click image to see larger view.) |
Speed up Web access with a HOSTS file
There's another way to speed up DNS -- by creating or editing a local HOSTS file on your own PC that contains URLs (also called hostnames) and their corresponding IP addresses. Windows will first look there to see whether there's an entry for the hostname, and if it finds it, it will resolve the address itself. That way, you won't have to go out to a DNS server and wait for the response before visiting a Web site.
The HOSTS file is a plain-text file you can create or edit with a text editor like Notepad. You should find an existing HOSTS file in C:\Windows\System32\Drivers\Etc\HOSTS in both Windows XP and Windows Vista. (In some versions of Windows, it may be located in C:\Winnt\System32\Drivers\HOSTS). The file has no extension; it is named only HOSTS. If you don't find one, create it in Notepad.
Open the HOSTS file in Notepad and enter the IP addresses and hostnames of your commonly visited Web sites, like this:
65.221.110.98 computerworld.com
Each entry in the file should be on one line. The IP address should be in the first column, and the corresponding hostname in the next column. At least one space should separate the two columns. When you're finished editing the file, save it to its existing location.
Make sure to check your HOSTS file regularly and keep it up-to-date, or else you might deny yourself access to certain Web sites. For example, if www.computerworld.com were to change its IP address but your HOSTS file kept the old, incorrect address, your browser would not be able to find the site.
Adjust Windows' DNS cache
To speed up DNS, Windows puts the DNS information into a local DNS cache on your PC when you visit a site. So when you want to go to a site, Windows first looks in its local DNS cache, called the resolve cache, to see whether the DNS information is contained there. That way, if it finds the information locally, it doesn't have to look in your HOSTS file or query a remote DNS server to find IP information. The cache is made up of recently queried names and entries taken from your HOSTS file.
The cache contains both negative and positive entries. Positive entries are those in which the DNS lookup succeeded and you were able to connect to the Web site. When Windows looks in the cache, if it finds a positive entry, it immediately uses that DNS information and sends you to the requested Web site.
Negative entries are those in which no match was found, and you end up getting a "Cannot find server or DNS" error in your browser. Similarly, when Windows looks in the cache and finds a negative entry, it gives you the error message without bothering to go out to the site.
Negative entries can lead to problems. When you try to make a connection to a site that has a negative entry in your cache, you'll get an error message, even if the site's problems have been resolved and it's now reachable.
You can solve this problem, though, using a Registry hack. By default, Windows caches negative entries for five minutes. After five minutes, they're cleared from your cache.
But if you'd like, you can force Windows not to cache these negative entries so that you'll never run into this problem. Run the Registry Editor by typing Regedit at a command prompt or the Windows Vista search box, and press Enter. Then go to
HKEY_LOCAL_MACHINE\SYSTEM
\CurrentControlSet\Services\Dnscache
\Parameters
Create a new DWORD value with the name NegativeCacheTime and give it a value of 0. (The value might already exist. If it does, edit its value to 0.)
The DWORD determines how much time, in seconds, to keep negative entries in the DNS cache. If you like, you can have the entries stay alive for one second by giving the DWORD a value of 1.
After you're done editing, exit the Registry. To make the change take effect, restart your computer, or flush your cache by issuing the command ipconfig /flushdns at a command prompt. The command will flush your DNS cache -- all the entries, both positive and negative, will be flushed -- and it will be empty until you start visiting Web sites. Negative entries, however, will not be added to the cache if you've given the DWORD a value of 0.
You can also use the Registry to control the amount of time positive entries are kept in the DNS cache. By default, they are kept for 24 hours. To change the default, go to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters again and create a DWORD value called MaxCacheEntryTtlLimit. (If it's already present, just edit the value.) For the value, enter the amount of time you want the entry to remain, in seconds, making sure to use decimals as the base.
If you run into other DNS problems, see the related story, "Fix your DNS problems."
Note: Some of the content for this article was taken from my upcoming book The Big Book of Windows Hacks and from Windows XP Hacks.
Yahoo to Support OpenID Single Sign-On
Posted On Friday, January 18, 2008 at at 1/18/2008 11:23:00 PM by nullYahoo user names and passwords will be used to access Web sites that support the OpenID 2.0 digital identity framework, starting January 30.
People with a Yahoo user name and password will be able to use that ID information to access non-Yahoo Web sites that support the OpenID 2.0 digital identity framework, reducing the amount of different log-in information people need to create, remember and enter online.
Already, almost 10,000 Web sites support OpenID, an open framework available for free to end users and Web site operators alike, according to the OpenID Foundation.
Yahoo's move will triple the number of OpenID accounts to 368 million by adding its 248 million active registered users to the rolls, the company said Thursday.
OpenID addresses one of several issues related to giving people more control of their online activities. Other groups are focusing on data portability, to let people move around the data and content they create online, so that they don't have to enter it manually in, say, every social-networking site they sign up for.
Yet other initiatives, like Google's OpenSocial, aim to create standard interfaces so that developers can create applications that run in multiple social-networking sites, instead of having to rewrite the same application multiple times for every site.
For all of these initiatives, it's critical for major Internet players to get involved, so that the benefits of standard technology and methods developed by groups like OpenID can have a real-world impact.
Unsurprisingly, in Thursday's statement, Scott Kveton, the OpenID Foundation's chairman, hailed Yahoo's support as a crucial validation of the framework that will help spur its adoption by other large Web site operators.
Other major players that have expressed interest and gotten involved in varying degrees with OpenID include Google, Six Apart, AOL, Sun, Novell and Microsoft.
Yahoo's announcement doesn't come as a complete surprise, since signs that it had been working on an OpenID implementation had surfaced. For example, a short message in the domain me.yahoo.com indicating the company would act as an identity provider for OpenID was spotted last week.
Yahoo participated in the development of version 2.0 of the OpenID framework, which the company said provides new security features. Yahoo users who log in to third-party OpenID sites should know that the log-in process doesn't reveal e-mail or instant-message addresses, Yahoo said Thursday.
Yahoo's initial OpenID service will be available in public beta on Jan. 30 and the company is working with several partners, including Plaxo, so that the Yahoo ID will work on their sites that day.
Anti-spammer fined $60K for DNS lookup 'hack'
Posted On at at 1/18/2008 11:22:00 PM by nullDavid Ritz, the veteran American spam-fighter, has been hit by $60,000 in fines plus lawyers fees after losing a civil suit that accused him of illegal hacking.
Sierra Corporate Design, a North Dakota business run by alleged former spammer Jerry Reynolds, sued Ritz for hacking and trespass offences. Ritz was accused of conducting unauthorized whois and DNS lookups. Edward Falk, another anti-spam campaigner and operator of the "Spam Tracking Page", was named as co-defendant.
The complaint alleged that Ritz "hacked" servers owned by Sierra (which describes itself as a specialist web hosting and internet services firm), obtaining confidential internal network configuration data (using a zone transfer, host -l command) and domain name information (using whois) before publishing that data on the net. It was alleged that Falk assisted Ritz by republishing his findings. The case was originally filed in May 2005. An injunction, which allowed Sierra's lawyers to ask Google to purge its Usenet archives of "offending material" was issued in August 2005.
In October 2006, the North Dakota court ruled that it did not have jurisdiction over Falk, a Californian resident, dismissing the suit against him. The case against Ritz proceeded.
Hearings in Fargo last October before Judge Cynthia Rothe-Seeger resulted in a surprise 11 January ruling (PDF, transcript with commentary) against Ritz. He was ordered to pay $53,000 in damages, a $10,000 fine for contempt against breaching an injunction and lawyers' fees, which could run into tens of thousands.
It's unclear if Ritz intends to appeal. His problems don't stop there because he faces possible criminal prosecution over the same supposed offences.
The case has sparked concern and support from the anti-spam community. "He [Ritz] got prosecuted for using the same Unix tools that the rest of us use all the time to troubleshoot problems, admin our systems, and track spammers," notes Reg reader Mark.
Supporters are urged to donate to a legal defense fund, set up to defend anti-spam activists against so-called SLAPP lawsuits (getting sued for speaking out on a matter of public concern).
In a separate case Reynolds sued Falk unsuccessfully for defamation for calling him a porn spammer.
Falk had accused Reynolds of involvement with Netzilla, for a time the single largest source of spam on Usenet. The published allegations led to the unsuccessful "John Doe" lawsuit against Falk in Reynolds' home town of Fargo, ND.
More background on the history of legal antagonism between Falk and Reynolds can be found at Falk's site here and elsewhere.
iTunes movie rental hack keeps the good times playing
Posted On at at 1/18/2008 11:21:00 PM by null
Image courtesy of Gizmodo
Apple's terms for iTunes Store movie rentals seem pretty reasonable. Customers have 30 days to begin watching the film they rent, then 24 hours to finish it after first clicking play. Naturally, some users out there always want more, and a simple new hack involving a little time travel can help extend the time you can keep and watch iTunes Store movie rentals.
As TUAW found, all users need to do is push their system clock into the future to trick iTunes into extending the time one has with a rented movie. Gizmodo later confirmed that setting one's clock ahead by at least a year, clicking play on a movie, then coming back to the present will stretch out the time one actually has to watch it, skirting both the 30-day and 24-hour limits.
It's pretty surprising that such a simple hack can defeat this terms system so easily, especially considering how obsessed the studios are with protecting their content. After Steve Jobs' open letter on music, we learned that Apple has two weeks to plug any flaws discovered that allow customers to get around music DRM, otherwise the music labels have the right to pull out of the store. You can bet your bottom dollar that the movie studios have a same or at least similar contract with Apple, so we wouldn't recommend trying to build a new movie collection with this a trick like this. Look for the hack to get plugged soon.
Microsoft warns of Excel flaw
Posted On at at 1/18/2008 11:21:00 PM by nullMicrosoft is warning users of a flaw in Excel which is already being targeted by hackers.
The company has received reports of attacks attempting to exploit the vulnerability via email.
In order to launch the attack, users must manually launch the malicious file.
A successful exploit could allow the attacker to access the machine with the same rights as the current user.
The flaw affects Excel 2003 Service Pack 2, Excel Viewer 2003, Excel 2002, Microsoft Office Excel 2000 and Excel 2004 for Mac.
Excel 2003 Service Pack 3, Excel 2007 and Excel 2008 for Mac are not believed to be affected by the vulnerability. The Microsoft Office Isolated Conversion Environment protects against the attack.
Microsoft said that the attacks were launched against specific targets, rather than random users.
Because the attack only grants the permissions of the current user, Microsoft said that administrators can minimise the risk by restricting user rights.
The US Computer Emergency Response Team urged users to mitigate the risk of attack by not opening suspicious email attachments.
Online crime gangs embrace open source ethos
Posted On at at 1/18/2008 11:20:00 PM by nullAdd the malware bazaar to the list of marketplaces being radically reshaped by the forces of globalization.
That's the conclusion of Thomas Holt, a professor of criminal justice at the University of North Carolina at Charlotte, who says the marketplace for rootkits, Trojans and other software nasties increasingly transcends national boundaries. In many respects, malware creation mimics open source communities, in which legions of programmers spanning the globe tweak one another's code to add new features and fix bugs.
"It seems somewhat different than the standard way of thinking of a hacker," says Holt, who presented his findings Thursday to military and law enforcement officials at the US Department of Defense's Cyber Crime Conference. Crime groups "are looking to one another for assistance. It's no longer just a single person distributing malware. Now there appear to be groups and there appears to be a distribution of labor."
Holt and a team of researchers scour websites, internet relay chat channels and other online forums where malware is discussed and distributed. What they're seeing is a collaborative process in which a title is released by a hacker in one region and then re-released again and again over the next several years in different locales by other authors.
Take, for example, the distribution, of Try2DDoS, a tool that automates distributed denial of service attacks. It was first released in June 2005 on Underground Konnekt, a hacker website operating out of France, by a user dubbed Libere_ton_espri.
Over the next two years, a program with the same name and containing identical source code turned up on boards in China, Guatemala, Russia and Argentina and then again in China. As the program moved, it gained new capabilities, including support for Spanish and Chinese languages.
The comparison to open source development only goes so far. Three of the four individuals reposting the program claimed to be the original authors, something Libere_ton_espri or no one else bothered to challenge.
To be fair, collaboration among online miscreants isn't exactly new. The Rbot Trojan and countless other pieces of malware have been passed around the net and modified by script kiddies and seasoned criminals for years. What Holt seems to be saying is that the shift of malware creation from sport for bragging rights to profit-driven enterprise means authors aren't as upset when their work is plagiarized by a rival group. The profit motive also seems to have brought a pragmatism to the activity, making criminals more willing to collaborate with one another.
The research carries important lessons for law enforcement officers and others on the front lines of computer security, to whit: that it's often difficult to know who is the original creator of a piece of malware making the rounds. More importantly, it shows that malware takes on a life of its own once it is released into the wild. Tracking down a programmer or group responsible for its creation doesn't mean the crimeware is likely to go away.
Social networks are one way cyber gumshoes can learn more about people engaged in the creation and trafficking of malware. Holt says his group recently found a programmer from Eastern Europe providing surprisingly detailed accounts of his life on one site. It included a picture of his computer work space and information about his apartment, roommate and a next-door neighbor. He even volunteered information about an alcohol problem. (Holt declined to provide specifics because he says he is working with law enforcement officers to track down the individual.)
Of course, some online crime groups are more tight-lipped than others. Groups behind malware branded the Storm Worm and the so-called Rock Phishing attacks are notoriously secretive, likely making the monitoring of social networks of little value to people tracking such them.
Still, in many cases, it can prove a bonanza.
"Not only can you find information about the person creating the tool," Holt says. "You can find a little about their motivation, whether it's political or economic. It can give you some real insight into the person and that's got some real weight to it
DHS Testing Three Anti-Missile Systems for Commercial Planes
Posted On Thursday, January 17, 2008 at at 1/17/2008 11:12:00 PM by null Homeland Security's technology research and development arm is looking into three different sophisticated -- and expensive -- technological solutions that can counter a shoulder-launched missile attack against commercial airplanes, spurred on, despite the high cost, by the increasingly sophisticated nature of such attacks in Iraq.
Homeland Security's technology research and development arm is looking into three different sophisticated -- and expensive -- technological solutions that can counter a shoulder-launched missile attack against commercial airplanes, spurred on, despite the high cost, by the increasingly sophisticated nature of such attacks in Iraq.
DHS recently announced that three American Airlines planes would be outfitted with Pentagon-developed onboard sensors and high-powered laser countermeasures to figure out how much maintenance the units will need under regular use, according to James Tuttle, the director of Homeland Security's Science and Technology research division. That test happened through a $29 million grant and a partnership with BAE Systems.
Shoulder-launched missiles, known as MANPADs in military parlance, have been fired overseas against commercial flights, but never domestically. A DHL plane was successfully struck in Iraq in 2003 by such a missile, but it did not destroy the plane since it hit a wing-mounted engine. The government estimates some 5,000 MANPADs are loose in the world, some of which were provided by the U.S. to Afghanis fighting the Russians who invaded.
Tuttle spoke about his division's efforts at the DHS S&T Stakeholders Conference in Los Angeles on Wednesday.
DHS tested the system in Nevada, where testers shot 50 different missiles at the plane and the military-developed system proved it was capable, according to Tuttle.
"The issue is how much it would cost to maintain the system if we put it on all 600 widebody aircraft in the United States," Tuttle said.
While Congress is bulllish on the systems, the airlines aren't convinced the system is necessary or that it will be cost efficient. DHS's own initial risk assessment also concluded that the costs outweighed the risks, but began exploring solutions further after being told to do so by Congress.
That deployment would cost some $600 million up front, but the maintenance costs and lifecycle of the units are unknown, which will be a key factor in Congress's ultimate decision to fund or postpone the technology's deployment to civilian aircraft.
DHS is also looking into two other possibilities -- one a plane flying at 50,000 feet -- above FAA-controlled airspace -- that could detect a shoulder-fired missile and disable it from above with a high-powered laser blast. But that approach runs into problems with cloud cover. Additionally, that system would be firing at the homing eye of the missile at an steep angle, rather than straight-on like the plane based system, making the targeting harder and requiring a more high-powered blast, according to Tuttle.
DHS tested a prototype-plane with detection technology at the same time it tested the plane-based system. Using NASA's version of the high-flying U2 spy plane, DHS found that the system worked well at detecting threats, and Tuttle said the planes fly high enough that one plane could cover multiple airports that are geographically close -- such as Baltimore's airport and D.C.'s Ronald Reagan and Dulles airports.
The third possibility involves using a ground-based system. That solution, however, runs into problems about space at airports and what the strength of its laser's blast will have on passengers' cell phones and pacemakers, as well as the plane's electronics, Tuttle told THREAT LEVEL.
One other trouble with airplane-based deployments is what do about foreigners, Tuttle said. What should be the requirements for foreign planes or U.S. planes flying internationally, given this is considered critical and sensitive technology that the U.S. would not want in the hands of foreign governments.
Tuttle says that Congress, not DHS, will make final decisions.
"We are developing technology," Tuttle said. "That is all we can do."
(Note to long-time readers, his name is Tuttle, not Buttle.)
FBI takes biometrics database proposal to U.K.
Posted On at at 1/17/2008 11:12:00 PM by nullPolice in the U.K. are in talks with the FBI about establishing an international biometric database for tracking down the world's most wanted criminals and terrorists.
The so-called "server in the sky" database would share criminals' biometric data, such as fingerprints and iris scans, internationally. The Washington Post reported last month that the FBI is spending $1 billion to develop the world's largest centralized biometrics database, a system the agency calls Next Generation Identification.
The FBI suggested the database at a meeting of five countries--Australia, Canada, New Zealand, the U.K., and the U.S.--in the International Information Consortium technology group.
The U.K.'s National Policing Improvement Agency said it was aware of the proposal and that any such system could be linked into existing law enforcement databases such as Ident1, the U.K. repository of more than 7 million pieces of biometric data from crime scenes, although there are no formal plans for such an initiative at the moment.
"The FBI are proposing this and the proposals are being discussed by the International Information Consortium group, but these are initial discussions; there are no agreements," a spokesman for the NPIA said.
The Home Office, the U.K. government department for law enforcement and public safety, also confirmed it was aware of the FBI database project as one of a "wide range of initiatives we are constantly looking at to improve our investigative capabilities."
U.S. defense company Northrop Grumman, which built the Ident1 system, also confirmed it had spoken to the FBI about the server-in-the-sky database.
The announcement of the database proposals follows the news earlier this week that the U.K. has completed a system to check the fingerprints of every visa applicant.
The FBI was unavailable to comment at publication time.
FBI warns of malicious email scam
Posted On at at 1/17/2008 11:11:00 PM by nullThe FBI has issued a warning to the public following a deluge of spam emails purporting to be from the agency.
The bogus messages often include pictures of FBI director Robert Mueller, along with the organisation's official seal, letterhead and banner.
"The FBI does not send out emails soliciting personal information from citizens," said the agency.
"The social engineering technique of using the FBI's name is designed to intimidate and convince the recipient that the email is legitimate.
"Please be cautious of any unsolicited email referencing the FBI, Robert Mueller or any other FBI official endorsing any type of internet activity."
The emails are typically a notification of a 'lottery win' or long-lost relative leaving an 'inheritance'.
Other emails offer website monitoring containing malicious attachments, and online auction scams.
The warning comes just six months after the FBI issued a similar alert about spammers using trusted institutions to improve returns.
Mystery web infection grows, but cause remains elusive
Posted On at at 1/17/2008 11:11:00 PM by nullThe mystery over a cluster of poisoned websites distributing a toxic malware cocktail may be better understood but it's still not solved.
Five days ago, we wrote about the infection of several hundred websites that was unlike anything seasoned researchers had seen before. Mary Landesman, a cyber gumshoe who first brought it to public attention, asked for help from other security pros in figuring out how the unusual new technique worked. And help is what many of her peers have provided.
The sites host malicious javascript that is spontaneously created and randomly named only after a visitor hits the home page. That's unlike any other mass infection most researchers have seen before. Usually, infected sites merely host pointers to attacker-controlled servers, which in turn are used to host malware with static file names.
The innovative technique is much more than an academic curiosity. Because the rogue code does not exist on any server until an end user visits it, the javascript remains invisible to site administrators. The randomness also prevents most antivirus programs from detecting the javascript. Equally frustrating, it prevents researchers from running a simple web search that ferrets out every web address where the attack code is hosted.
From her perch at ScanSafe, a company that provides real-time intelligence to large businesses about malware-spreading sites, Landesman could see several hundred websites exhibiting the odd behavior. Based on intelligence from firms with sensors elsewhere on the net, it turns out that the number of infected sites is much bigger.
According to independent reports released earlier this week by SecureWorks and Finjan, 10,000 or more websites are similarly infected. As of Tuesday, almost all of these were still infected. They are churning out malware, which preys on at least nine different vulnerabilities in programs such as the QuickTime media player, Yahoo! Messenger and Windows operating systems to install a backdoor on end users' computers.
Alive and kicking
Attackers "want to have their malicious code live and kicking for a longer time so it will be much more difficult to identify that this website was compromised," says Yuval Ben-Itzhak, chief technology officer at Finjan, a security provider that's been monitoring the attacks since December. "The longer they will have the malicious code out there, the better the chances they'll infect people."
Once the malware successfully finds an unpatched vulnerability, it installs the Rbot Trojan, or one of its variants. Many antivirus programs still fail to detect the exploit.
The infection dates back at least to late November, according to this thread, which was dredged up by a Reg reader in response to our earlier story. The online discussion shows web administrators from many companies reporting infections that were using multiple exploits to attack end users, and documents their difficulty in disinfecting the systems.
Landesman also reports how hard it is to remove the attack code from tainted web systems. Over the weekend, she noticed two modules - one called mod_bwlimited and the other enable_dl - in the Apache webserver that were responsible for transmitting the randomized malware onto end users' machines. But when she disabled them, she was dismayed to find the changes reversed and that the machines had soon resumed their attacks.
Initially, ScanSafe and SecureWorks researchers suspected the attacks were the result of a web-side rootkit that creates and delivers the randomized files after a victim visits the site. After an earlier version of this story was published, however, Don Johnson of SecureWorks called to say he no longer believes that is the case.
Instead, he says, attackers have managed to install an Apache runtime patch onto the infected machines. The patch launches code into the Apache memory that monitor requests and transmits the randomly named payload into the response data. Apache modules generally have the ability to load or unload new modules without root access, and that seems to be the case here.
But so far no-one - not ScanSafe nor SecureWorks, Finjan or any other researcher we've contacted - knows for sure how these mostly mom-and-pop ecommerce sites are getting infected in the first place. The vulnerability is unlikely to reside in Apache, given the sheer number of variants that different infected machines are running.
Access all areas
Infected sites also use a wide number of different web hosts, making that an unlikely entry way for attackers. While Cpanel, a tool for remotely administering the site, appears to be modified by the infection, Landesman says her research suggests that is also not the way attackers gain access.
This is a problem, because if you don't know how thousands of of machines are being commandeered, you can't prevent tens of thousands more from suffering the same fate.
"Every time I think I have some common thread, I find some exception to the rule," says Don Jackson of SecureWorks. "How do we stop websites from experiencing this again? We really don't know what controls we need to put in place."
If Jackson's theory about the runtime patches proves correct, it's likely they were installed using compromised passwords for FTP servers or hosting applications connected to the infected web server. He posits a modified dictionary attack could have been the initial way in.
What's really needed now is for operators of websites that are infected to step forward and allow a trusted researcher to inspect the machine. (One webmaster from a site mentioned in Friday's article volunteered to help Landesman, but by then he had already wiped his system clean, removing crucial evidence in the process.)
If you've seen the behavior described above lurking on your site, please leave a comment below, or contact your reporter using this link. Similarly, if you're a researcher with insight into this program please do the same.
With a little more digging, we'll solve this mystery.
Excel Vulnerability Affects Windows And Mac Users
Posted On at at 1/17/2008 11:10:00 PM by nullMicrosoft (NSDQ: MSFT) on Tuesday posted a security advisory warning of a vulnerability in several versions of Microsoft Office Excel that affects both Windows and Mac OS users.
The affected versions include Microsoft Office Excel 2003 Service Pack 2, Microsoft Office Excel Viewer 2003, Microsoft Office Excel 2002, Microsoft Office Excel 2000, and Microsoft Excel 2004 for Mac.
Microsoft said that Microsoft Office Excel 2007, Microsoft Excel 2008 for Mac, and Microsoft Office Excel 2003 Service Pack 3 do not appear to be vulnerable.
"At this time, Microsoft is aware of specific targeted attacks that attempt to use this vulnerability," said Tim Rains, security response communications lead for Microsoft, in an e-mail. "Microsoft is aggressively investigating the public reports and customer impact."
Because the flaw is believed not to be widely known, Microsoft considers the risk to be limited.
The attack relies on a maliciously crafted Excel file that contains malformed header information. Attempting to open the file, either through a Web browser or as an e-mail attachment, can corrupt system memory, which could give an attacker the opportunity to execute remote code on the victim's system or to obtain elevated user privileges.
"In a Web-based attack scenario, an attacker would have to host a Web site that contains a specially crafted Excel file that is used to attempt to exploit this vulnerability," Microsoft said in its advisory. "In addition, compromised Web sites and Web sites that accept or host user-provided content could contain specially crafted content that could exploit this vulnerability. An attacker would have no way to force users to visit these Web sites. Instead, an attacker would have to persuade users to visit the Web site, typically by getting them to click a link in an e-mail message or instant messenger message that takes users to the attacker's site."
Both Microsoft and US-CERT, part of the national cyber security division at the Department of Homeland Security, recommend that Microsoft Office users not open unexpected e-mail messages with attachments or messages from unfamiliar sources.
In a blog post, Microsoft said it is working on a fix that will be released either as part of its regular patch schedule or in an out-of-band release, depending on the impact of the vulnerability.
Legitimate sites serving up stealthy attacks
Posted On Wednesday, January 16, 2008 at at 1/16/2008 05:48:00 AM by nullThe attack, dubbed the "Random JS toolkit" by the security firm, currently uses dozens of hosting servers and more than 10,000 legitimate domains to attempt to exploit the systems of visitors to the sites, the company said in an analysis posted to its Web site. The compromised sites host the malicious code -- foregoing the iframe redirect that has increasingly been used by attackers -- and serves up the attack to each visitor only once using a random file name each time. The two techniques, along with more traditional code obfuscation, makes the attack difficult to find, said Yuval Ben-Itzhak, chief technology officer for Finjan.
"This attack uses three different methods to go undetected by signature-based or URL-based defenses," Ben-Itzhak said. "If you realize that you've been infected, and you go and search sites, you will not be able to find the site that infected you."
The Random JS toolkit attack is the latest malicious code to use two stages: First, infecting a Web site with an infection kit or iframe tag and, second, attempting to exploit the systems of visitors to the compromised sites. Last week, several security researchers warned users of an attack in which infected Web sites would be injected with a snippet of Javascript code encapsulated in an iframe which would then redirect visitors to at least two domains, uc8010.com and ucmal.com, hosting malicious code.
Security firm Finjan first detected the Random JS Toolkit in mid-December and spent the rest of the month analyzing the code, Ben-Itzhak said. Previous attacks have used random Web page names to foil defenses based on keeping track of malicious Web addresses, or URLs, and used a database of Internet addresses of known Web crawlers to attempt to avoid tipping off security firms. However, the Random JS toolkit is the first malicious software to marry these two techniques so successfully, Ben-Itzhak said.
A client-side honeypot -- or honeymonkey, as Microsoft calls them -- could detect the Random JS attack from a specific Web site, but if a second machine using the same Internet address returns to the site, it would not receive the malicious code. The sites infected by the Random JS toolkit include pages at the University of California, Berkeley's Web site and Teagames.com, according to Finjan.
The attack is a logical progression of the techniques used by attackers on the Web, said Roger Thompson, chief research officer for antivirus firm AVG.
"The 'single copy to single person' is to make it hard for researchers to get a crack at it," he said. "That has been done since the WebAttacker days of 2005. What it means is that (researchers) have to get (their) snapshots down the first time and have a pool of addresses to get a second and third copy of the program."
Antivirus companies have increasingly had to deal with the influx of variants for each threat generated by obfuscation code, Thompson said. By the end of 2007, the total number of variants of computer viruses, worms and Trojan horses had climbed to between 360,000 and 500,000, according to numbers released by two antivirus firms in the past month.
The actual malicious code served to visitors by the sites compromised by the Random JS Toolkit attempts to exploit computers using 13 different vulnerabilities, the company said. The Trojan horse program steals the victim's login credentials to access online banks. The software uses encrypted communications to a number of sites hosted in the United States to return the information to the criminal group behind the attack, the analysis found.
While Finjan's analysis underscored the difficulty in detecting the toolkit, AVG's Thompson stressed that defenders would quickly adapt.
"It is likely another kit, like the MPack and IcePacks of the world," Thompson said. "It is not startling, just interesting... and another part of the puzzle that further indicates that the Web is the emerging battleground."
Finjan did not attempt to determine how well current antivirus software performed in detecting the malicious Trojan horse used by the Random JS toolkit. Symantec, a competitor to Finjan and AVG, owns SecurityFocus.
Mac Security Program a Scam?
Posted On at at 1/16/2008 05:48:00 AM by nullThe MacSweeper site purports to scan Macs for security issues, then sell users a software fix--but researchers have their doubts.
Some Macintosh users have encountered a security program whose function and Web site have the tell-tale signs of a scam.
Visitors to the Web site selling the program, called MacSweeper, are offered a free security scan of their computers. The scan, which only works on Macs, highlights supposed security problems with the computers. It offers to remove the problems with the purchase of a US$39.99 lifetime subscription.
But the awkward English on the program's Web site, and the way the program operates, have raised doubts over its legitimacy, users and security researchers say.
"The imbibed set of features locates all the junk and useless data on your computer and deletes them to reclaim the wasted space," according to the pitch on MacSweeper's home page.
Security company F-Secure wrote on Tuesday that the program, called MacSweeper, may be the first rogue application for Macs.
Windows machines have been more frequently targeted by similar software, sometimes labeled "scareware" since users are warned their computers will be in danger unless they purchase the software. Among the more notorious scareware for PCs is Winfixer, also known by the aliases ErrorSafe, WinAntiVirus and DriveCleaner.
The MacSweeper Web page is hosted on a server in Kiev, Ukraine, said Patrik Runald, security response manager for F-Secure, who is based in Malaysia. Information on the site about MacSweeper's company, Kiwi Software, has been plagiarized from Symantec's Web page, Runald said.
"They just ripped that information straight off there," Runald said.
The same text is also used on Cleanator.com, which sells a Windows-compatible version of the same kind of program, Runald said. Another security vendor, Sophos, classifies Cleanator as a "potentially unwanted program."
Once MacSweeper is running on a Mac it will often pick odd items, such as language files, and label them as being a privacy risk, Runald said.
In at least one instance an F-Secure researcher visited the MacSweeper site and clicked a button labeled "Free scan." The scan highlighted Mac-related problems, even though the researcher was using a PC.
MacSweeper doesn't use any tricks to get onto a machine other than trying to persuade users to download it, Runald said. Nonetheless, F-Secure typically contacts Finland's Computer Emergency Response Team when it finds scams such as MacSweeper, Runald said.
A user on one of Apple's discussion boards wrote that their Safari browser kept redirecting to the MacSweeper site, a sign that malicious scripts may be involved.
"If I click on anything it'll try downloading the software," the person wrote. "How do i get rid of this? It's really annoying. I don't want it, and I'd wish it would leave me alone."
US spy chief puts security over privacy
Posted On at at 1/16/2008 05:46:00 AM by nullThe Director of National Intelligence, who oversees all 16 US intelligence agencies, has revealed the extent to which domestic and international internet traffic is being monitored.
Mike McConnell, who advises President Bush directly on security issues, said in an article in the New Yorker that privacy will have to take a back seat in the name of security.
McConnell gave details of a proposed cyber-security policy which will closely police internet activity.
Lawrence Wright, the article's author, claimed that Ed Giorgio, a former chief code breaker at the National Security Agency who is working with McConnell on the plan, had told him that this would mean giving the government the authority to examine the content of any email, file transfer or web search.
"Google has records that could help in a cyber-investigation," said Wright. "Giorgio warned me that 'privacy and security are a zero-sum game'."
McConnell, who keeps a clock on his desk counting down the seconds of the Bush presidency, admitted that the plans would be a tough sell to the legislature but insisted that they are necessary.
"My prediction is that we are going to screw around with this until something horrendous happens," he told Wright.
Wright suggested that this kind of monitoring is already going on. He spoke to an AT& T employee, Mark Klein, who claimed that he installed data switching systems in the company's exchange that copied all internet traffic to the National Security Agency.
"I know that whatever went across those cables was copied and the entire data stream was copied," said Klein. "We are talking about domestic as well as international traffic."
He added that previous claims by the Bush administration that only international communications were being intercepted are not accurate.
"I know the physical equipment, and I know that statement is not true," said Klein. "It involves millions of communications, a lot of it domestic communications that they are copying wholesale."
Military industrial complex aims to revamp email
Posted On at at 1/16/2008 05:22:00 AM by nullA consortium of British and US military agencies and defense and aerospace firms have agreed a new standard for secure email. Security experts are watching the developments closely, but are unsure how much of the specification will make it into public use or commercial email security products.
The secure email specification from the The Transglobal Secure Collaboration Program (TSCP) aims to address email's inherent identity and data transmission security flaws. The specification covers a method for authenticating users that creates a Public Key Infrastucture system that could act as the backbone for other forms of electronic collaboration.
The requirements were defined and endorsed by the members of the TSCP: the US Department of Defense (DoD), UK Ministry of Defence (MoD), BAE Systems, Boeing, EADS, Lockheed Martin, Northrop Grumman, Raytheon, and Rolls-Royce.
The US Defence Department intends to use the specification to protect "controlled but unclassified information". The MoD also expects to deploy the capability enterprise-wide in 2008 for classifications up to "UK Restricted".
The TSCP implementation is based on TSCP-defined publicly available specifications which organisations must follow to assign vetted identity information to all email senders and recipients. The current implementation was constructed with commercial-off-the-shelf (COTS) products, open source software, and a commercial trusted third-party service, CertiPath. The resulting digital certificate-based system ensures that information only travels to and from trusted parties. The framework plugs into either Lotus Notes or Outlook clients.
PKI has long been touted as the next big thing in information security. But the difficulty of putting in such systems and integrating them with other platfors has made the technology complicated and costly. Even though most aspects of the TSCP approach are public, it's unclear how much impact the approach will have in the wider world outside military organisations and their contractors.
"I don't know how much of this will end up public. Certainly I'm interested. And certainly email could use a major security overhaul," security guru Bruce Schneier told El Reg. "People are abandoning the medium in favour of others that are less spam-filled
US security agency leaks data
Posted On Tuesday, January 15, 2008 at at 1/15/2008 09:19:00 PM by nullThe US Transportation Security Administration (TSA) has been slammed by the House Oversight and Government Reform Committee for sloppy website security.
In a damning report the Committee identified major security leaks in a vital TSA web page that could allow personal information to be harvested.
Vulnerable details included name, address, Social Security number, birth date and place and even eye colour.
The Committee found that the TSA was not even hosted on government servers, as the website was outsourced to Desyne Web Services, a private contractor, in a no-bid contract.
The TSA employee who put out the tender is claimed to be a childhood friend of the owner and a former employee.
"There were multiple factors that contributed to security vulnerabilities in the TSA traveller redress website, including poor procurement practices, conflicts of interest and weak oversight," said the report.
"The result of these shortcomings was that an insecure website collected sensitive personal information from American travellers for months without detection by TSA."
The report found that the home and submission pages of the site, which was used by people appealing against being refused permission to fly, had no SSL encryption at all.
The site was not hosted on a secure government website, which caused confusion to users, and some pages were falsely listed as having third-party SSL certification.
The flaws were only fixed after Chris Soghoian, a Ph.D student, publicised them on his Slight Paranoia blog.
"[It is] incredible that they would take the site live using a self-signed certificate," Soghoian told the Committee.
"It shows major incompetence at Desyne. Someone is either too stupid or too cheap to purchase a real SSL certificate before putting up a site that asks for personal data. This is Web Development 101."
The problem started when the TSA was created and took control of the lists of people not allowed to fly over US airspace. The list contained just 16 names on 11 September 2001, but has since grown to over 70,000.
Mistakes were commonplace and misidentified terrorist suspects included Senator Ted Kennedy, several children (including some younger than a year old) and the singer Cat Stevens.
A Department of Justice investigation found that 43 per cent of people on the list were false positives.
The appeals process was paper based for four years and had three officers assigned, leading to a backlog of tens of thousands of applications.
The TSA moved the operation online but decided that it did not have the space to host the site and outsourced it to Desyne.
The Committee found that the Request for Quote was written in such a way that Desyne could be the only bidder, since it specified reuse of existing TSA code which only Desyne, as it already had $500,000 worth of existing business with the organisation, would have.
"TSA investigators found that the primary author of the April 2006 statement of work was the director of the Claims Management Office, Nicholas Panuzio," the report said.
"Panuzio told TSA investigators he had known Desyne's owner since high school, had worked for Desyne for eight months in 2001 and 2002, and still met regularly with Desyne's owner and others for drinks or dinner.
"Panuzio played a key role in the development of the traveler redress website. For example, one email exchange shows that the Redress Management project director, James Kennedy, relied on Panuzio's recommendation to pay Desyne's December 2006 invoice.
"Although he had earlier disclosed this conflict of interest to the TSA Office of Chief Counsel, Panuzio did not disclose it to the project manager or to the lead contracting officer on the project."
The Committee said that the problems on the site had now been fixed, and that it is being hosted by the Department for Homeland Security.
No action is being considered against Panuzio because he had not profited personally, or Desyne, which still hosts two TSA websites.
It has not been a good 12 months for the TSA. The organisation was forced to call in the FBI last year after it lost 100,000 staff records stored on an external hard drive.
Convicted Hacker Charged With Extortion After Attack On Model's MySpace Account
Posted On at at 1/15/2008 09:19:00 PM by null A Southern California man convicted last year of hacking into the Lexis-Nexis owned consumer database Accurint was arrested on charges on extortion Friday after allegedly hijacking the MySpace account of an internet celebrity.
A Southern California man convicted last year of hacking into the Lexis-Nexis owned consumer database Accurint was arrested on charges on extortion Friday after allegedly hijacking the MySpace account of an internet celebrity.
Jeffrey Robert Weinberg, 22, was arrested by LAPD detectives in Southern California early Friday morning, a department spokeswoman confirmed. While police aren't discussing the particulars, the arrest follows a detailed blog post by "Amor Hilton" an 18-year-old Los Angeles woman who says she helped detectives build a case against Weinberg after he hijacked her MySpace account and demanded nude photos and "phone sex" in exchange for its return.
Hilton's weekly live video show Bare Naked on the amateur streaming site Stickam has made her an online celebrity of sorts. She named herself for fashion model Nicky Hilton, sister of heiress Paris Hilton. Weinberg was one of a gang of hackers who penetrated Paris Hilton's cell phone account in 2005, the Washington Post reported last year.
According to her blog post, Hilton found herself locked out of her MySpace account on December 28th, the same day she began receiving harassing phone calls from a hacker calling himself "V.I.P." -- a handle used by Weinberg in the past. The calls continued over the course of several days, and often took a threatening tone, she says.
During that time, the hacker allegedly disconnected Hilton's cell phone account, and took over her account on Stickam. Stickydrama.com, a gossip site dedicated to Stickam celebs, published a photo of Hilton on December 29th, which it said was sent in by a self-described hacker who identified it as a private photo pilfered from Hilton's MySpace account.
Hilton reported the harassment to the police, and recorded one of the phone calls. She worked with LAPD detective Eric Jones to identify V.I.P. as Weinberg, she says, finally confirming it by comparing a mug shot to a photo the hacker had sent her.
"Don't mess with a Hilton," she wrote on January 3rd. "And that's how you catch a hacker."
 Weinberg was sentenced (.pdf) to 10 months in prison last year for hacking Accurint, and was released in November to begin three years of federal supervised release. Under the conditions of his supervision, he had to submit to random inspections of his computer hard drive, and was forbidden from possessing or using encryption software, among other restrictions.
Weinberg was sentenced (.pdf) to 10 months in prison last year for hacking Accurint, and was released in November to begin three years of federal supervised release. Under the conditions of his supervision, he had to submit to random inspections of his computer hard drive, and was forbidden from possessing or using encryption software, among other restrictions.
A source with ties to the computer underground says hackers have recently boasted about having access to MySpace's internal administrative tools. The source provided a screenshot of what appears to be a search page marked "confidential" that displays options not available on the service's public search -- including searching for MySpace users by their private internet IP address.
 A second screenshot shows what appears to be results from a search on actor Nicholas Cage, showing the IP addresses used to access three accounts bearing that name.
A second screenshot shows what appears to be results from a search on actor Nicholas Cage, showing the IP addresses used to access three accounts bearing that name.
A spokeswoman for MySpace did not return a phone call Monday. I'd love to hear from anybody familiar with MySpace's internal interfaces on the authenticity of these screenshots.
On Monday, MySpace reached an accord with 49 state attorneys that promises to tie off a year of inquiries into safety issues on the site, which followed my October, 2006, story on MySpace sex offenders. In that story I described how I used a PERL script to run the names and locations of approximately 400,000 registered sex offenders through MySpace's search engine, turning up 744 confirmable matches from one-third of the results. One of them, a thrice-convicted child molester, was openly courting young boys on MySpace, and was arrested as a result of the probe. MySpace then ran a more sophisticated search of its own and purged at least 29,000 past offenders from its roles.
In the deal with the state AGs, MySpace agreed to a laundry list of measures, such as removing the option for under-18 users to report themselves as "swingers," and setting underage users' profiles as "private" by default. The company is also forming a safety task force to explore options for online age and identify verification.
Denizens of the online hacker forum DigitalGangster have been chortling over Weinberg's arrest. "Weinberg likes to pick on people, internet celebs are like his calling," one poster wrote.
It's worth noting that Weinberg isn't universally liked in the underground, and newly-released cons are vulnerable to frame-ups. We'll wait watch to see how the case develops.
Weinberg's federal public defender didn't return a phone call Monday; a man who answered the phone at Weinberg's home in Dana Point, in Orange County, California, also confirmed that Weinberg had been arrested, but otherwise declined to comment or identify himself.
New Hack Attacks Can't Be Blacklisted
Posted On at at 1/15/2008 09:18:00 PM by nullReferring to the malware known as "random js toolkit," Andrew Storms, director of security operations for nCircle Network Security, said, "While a blacklist may help some users... it's no substitute for a good set of layered defenses... Security managers need to take a more active role in using management tools."
The security Relevant Products/Services firm Finjan says it has discovered a major new type of malware Relevant Products/Services that has infected more than 10,000 Web sites in December alone. Deemed "random js toolkit," it is a Trojan that infects end users' PCs and sends data from the infected machine to the "master" hacker. It can be used to steal passwords, documents and other sensitive information.
The malware dynamically creates and changes JavaScript code every time it is accessed, Finjan said. Thus, traditional anti-malware programs can't identify it.
Finjan CTO Yuval Ben-Itzhak said in a release, "Signaturing a dynamic script is not effective. Signaturing the exploiting code itself is also not effective, since these exploits are changing continually to stay ahead of current zero-day threats and available patches. Keeping an up-to-date list of 'highly-trusted-doubtful' domains serves only as a limited defense against this attack vector."
Dynamic Embedding
"What's needed to counter this exploit is dynamic code inspection technology that can detect and block an attack in real time," Ben-Itzhak said. "This technology doesn't depend on the origin URL, signature or the site's reputation, but inspects the Web content in real time, as served. It analyzes the code's intentions before enabling it be executed on the end-user browser."
Cyber criminals are intent on undermining trusted Web sites, Ben-Itzhak said. "In mid-year 2007, studies showed there were nearly 30,000 new infected Web pages being created every day. About 80 percent of those pages hosting malicious software or containing drive-by downloads with damaging content were located on hacked legitimate sites. Today the situation is much worse."
The attack works by dynamic embedding of scripts into a Web page, Finjan said. The dynamic embedding is done so selectively that "when a user has received a page with the embedded malicious script once, it will not be referenced again on further requests," the company said, so it can't be detected in forensic analyses.
Managers Must Be Proactive
"While dynamically changing malware is nothing new, this piece of code appears to be having some success in subverting the typical malware scanning systems," said Andrew Storms, director of security operations for nCircle Network Security. "While a blacklist may help some users... it's no substitute for a good set of layered defenses."
Storms added that this development shows Web site managers can no long play "the game of Whack-A-Mole." Rather, he said, "Security managers need to take a more active role in using policy and configuration management tools to ensure their Web sites and servers aren't vulnerable to attacks in the first place."
Among the 10,000 sites that have been infected are sites run by the University of California at Berkeley and Teagames Limited. Those organizations have been alerted, Finjan said, and the compromised sites are no longer online.
New mass hack strikes sites, confounds researchers
Posted On at at 1/15/2008 09:17:00 PM by nullA massive hack of legitimate Web sites has been spreading malware to visitors' PCs, using a new tactic that has made detection "extraordinarily difficult," security experts said today.
According to the researcher who broke the news, the hack, which involves several hundred sites, may be related to a November 2007 break-in at Fasthosts Internet Ltd., a U.K.-based hosting service that in early December acknowledged that some clients' log-in credentials had been pinched.
"All of the affected domains either have or have had a relationship in the recent past with Fasthosts," said Mary Landesman, a senior security researcher at ScanSafe Inc.
Like the large-scale hack prompted by a series of SQL injection attacks last week, the sites identified by ScanSafe are legitimate URLs, many of them small mom-and-pop e-commerce sites. Among them are a bicycle shop and several tightly focused travel sites, said Landesman. Most, although not all, are businesses located in the U.K.
But in almost every other way, this was a different, and much more sophisticated, attack. "Usually, in an attack like this, code is injected into the [site] pages, and that code is static," Landesman explained. "In these, it's completely different. The JavaScript that was being created and the reference [to it] was being generated dynamically."
That has given researchers, including Landesman, fits. In typical attacks, such as the SQL injection mass compromise, researchers can easily capture the attack code, analyze it and even use Google to search for other infected sites. Not so in this case.
"The method made it extremely difficult to tell who else might be impacted," Landesman said. "Here, the JavaScript was being generated dynamically and the file name was random, so we didn't have a common denominator. From a forensics standpoint, that hampers things greatly."
Paul Ferguson, network architect at Trend Micro Inc., seconded that. "It makes it extraordinarily difficult," he said.
The timing of those first attacks and the network break-in of Fasthosts was no coincidence, Landesman said. "The timing is what made me wise to the Fasthosts security breach," she said. "We've seen this attack vector only a couple of times since November 2007," the same month Fasthosts said it first noticed the theft of clients' passwords and usernames. "Timing is everything."
She speculated that, once armed with access to sites managed by Fasthosts -- the company's breach notification specifically mentioned that FTP passwords had been snatched -- criminals planted malware on the servers that they only recently activated. "Other malware is involved" that has aided and abetted the sites' hacks, said Landesman.
Visitors to the compromised domains have been assaulted with multiple exploits, notably one for a vulnerability in Apple Inc.'s QuickTime media player that was patched only last month. Another exploit being served, said Landesman, is the "tried and true" attack against Windows 18-month-old MDAC flaw.
If successful, the client-side attack infects the PC with a variation of the Rbot Trojan, a backdoor also known as Zotob that has been active since the middle of 2005. There, too, however, users are at special risk. "Just three out of 33 antivirus vendors detected that [variation]," Landesman claimed.
To top it all off, this hack's impact is magnitudes larger than the SQL injection's. "That accounted for just 1% of the blocks [ScanSafe instituted for its customers]," Landesman said. "This [new] one accounts for 18% of all blocks. That's a pretty tremendous number."
Fasthosts did not respond to a request for comment on a possible connection between its 2007 breach and the recent site compromises.
Confidential details fall off the back of lorries
Posted On at at 1/15/2008 09:13:00 PM by nullA box containing the banking details of 200 rich investors was found by the side of the road after apparently falling off the back of a courier's van.
The container, which included cheques and other sensitive papers, was supposed to be safely carried between a Prudential building in Reading to a secure storage facility in Essex by a DHL courier. Instead, it wound up close to a motorway slip road.
Financial details of 200 wealthy investors, including three national lottery winners, were exposed as a result. Luckily, the box was discovered by a vehicle recovery driver on a roundabout close to the slip road for Junction 11 of the M4 near Reading in Berkshire. The documents have since been returned to Prudential.
Preliminary results from an investigation into the incident suggests that the box fell out of a van door that the DHL driver had failed to properly close. Prudential has suspended the use of DHL as a courier until the investigation is over, This is London reports.
Prudential has written to affected customers, including Karen Child who won £8.4m on the Lotto last year, apologising for the breach. It promised its clients would not lose out as a result of the snafu.
Separately, the NHS has launched a probe after patient records on their way to disposal blew off the side of a lorry. Medical records of patients wound up strewn across a country lane in Hertfordshire, the BBC reports.
Whipps Cross University Hospital in Leytonstone, east London, and St Bartholomew's Hospital in the City, have each launched probes as a result of the breach.Poisoned MySpace page masquerades as Windows Update
Posted On Monday, January 14, 2008 at at 1/14/2008 09:44:00 PM by nullDoom watchers at McAfee have discovered a booby-trapped MySpace page that foists malware on users by spoofing a Microsoft update down the center of the profile.
The image (below) looks authentic enough to the drunk and uninformed. It is superimposed over the profile of a MySpace user who goes by the name of Rita. Clicking on the pic, or anywhere near it, initiates a download window that, if accepted, unleashes a malware cocktail that includes downloaders, Trojans and backdoors from multiple servers.
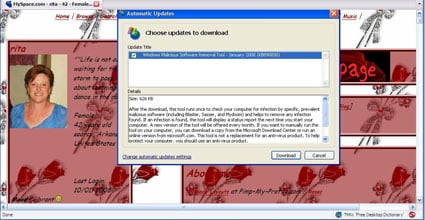
Attackers are sending friend requests to MySpace users in the hopes of getting them to click on the poisoned link. The downloads appear to come from Malaysia and the Ukraine.
McAfee researchers have contacted MySpace. The page, however, remained active as of time of writing of this article.
And so we find another strong endorsement for safe browsing practices. The Firefox extension NoScript won't save you this time, but common sense will. If a nubile hotty that's half your age and that you've never met sends a message asking to be your friend, odds are good you're being scammed.
Those running McAfee security software have a safety net. It recognizes the malware and stops its installation.New QuickTime Flaw Found
Posted On at at 1/14/2008 09:44:00 PM by nullBoth Windows and Mac versions of the multimedia program have a buffer overflow flaw that puts users at risk.
The United States Computer Emergency Readiness Team (US-CERT) has discovered a new buffer overflow vulnerability with Apple's QuickTime media software.
The vulnerability affects both Mac and Windows operating systems. Because QuickTime is part of Apple's popular iTunes jukebox software, that application is also affected, researchers said.
The vulnerability is found in the way QuickTime handles RTSP response messages. When attempting to display a specially crafted Reason-Phrase, QuickTime Player crashes at a memory location that can be controlled by an attacker, according to US-CERT.
The organization also said that they are aware of publicly available proof-of-concept code for this vulnerability.
US-CERT offers several solutions to the problem including uninstalling QuickTime, Blocking the RTSP protocol and disabling the QuickTime plug-ins in your Web browser.
Attackers targeted QuickTime in December in a separate RTSP vulnerability that Apple later fixed with a software update.
Apple representatives were not immediately available for comment.
Report: TSA Site Exposed Travelers To ID Theft
Posted On at at 1/14/2008 09:43:00 PM by nullA House of Representatives panel yesterday released a damning report about a Transportation Security Administration Web site built to address grievances from travelers errantly flagged by the government's no-fly list. It conlucded that cronyism and a lack of oversight exposed thousands of site visitors to identity theft.
The House Committee on Oversight and Government Reform began its investigation into security lapses at the TSA's Traveler Redress Web site last year, after Security Fix and other media outlets pointed out that the site accepted Social Security numbers and other sensitive information from travelers without encrypting the data, potentially allowing hackers to intercept the data. Wired.com noted in its coverage that the site was so laden in spelling errors that it resembled a phishing Web site, the sort typically set up by scammers to lure people into giving away personal and financial data.
The report, which liberally cites content and reader comments from Security Fix and Wired.com, found that the TSA awarded the contract without competition to Boston, Va based Desyne Web Services, and that the guy in charge of awarding the contract had previously worked at Desyne and was good friends with the owner. To date, Desyne has been awarded more than half a million taxpayer dollars worth of no-bid contracts by the TSA, according to the report.
The site's security weaknesses remained undetected by the TSA for more than four months, despite congressional testimony from TSA Administrator Kip Hawley that the agency had assured "the privacy of users and the security of the system" before its launch, the report notes. "Thousands of individuals used the insecure website, including at least 247 travelers who submitted large amounts of personal information through an insecure webpage."
Chris "Boarding Pass Hacker" Soghoian, the researcher and now cnet.com blogger who first discovered the TSA site screw-up, said half a million bucks is a lot of change for a few Web site forms.
"It's strange that with $500,000 in TSA's money, they couldn't afford a real SSL cert," Soghoian said.
This type of security oversight is unfortunately not as uncommon as you might think. On Wednesday, a reader tipped me off that the new member registration page for The Computing Technology Administration (COMPTIA) -- which requests credit card numbers in addition to other sensitive data -- was accepting new memberships and their credit card numbers without encrypting the data with Secure Sockets Layer (SSL) technology on the site. The security glitch was fixed within a few hours after I notified COMPTIA, but a COMPTIA spokesperson claimed that the organization had made no relevant changes to the site since my e-mail was sent.
Mass web infection leaves researcher scratching her head
Posted On at at 1/14/2008 09:42:00 PM by nullSecurity maven Mary Landesman is in the midst of piecing together a who-done-it involving the infection of hundreds of websites that are generating an enormous amount of traffic. Or maybe it's a how-done-it. Either way, she's mostly drawing blanks.
Landesman is a researcher for ScanSafe, a company that monitors the web surfing of employees at large companies and provides them with real-time intelligence about what sites are spreading malware. When a client visits a site that has already attacked someone else, the service automatically blocks the site from loading in the end user's browser. Viewing some seven billion web requests per month, company researchers see a fair amount of internet gremlins.
Over the past four days, 15 per cent of the blocked malicious traffic has come from just a few hundred sites, which appear to be legitimate ecommerce destinations that have been compromised by attackers. This prompted Landesman to do some digging, and what she uncovered is unlike anything she's seen before.
For one thing, the sites themselves are hosting the malware, which is then foisted on visitors. Most of the time attackers are unable to gain such a high degree of control over the sites they hack, so they redirect end users to servers under the control of bad guys and use them to drop malicious payloads.
"I'm stumped," Landesman says. "This is a very different method of infecting the user. I want to find out how they're doing it and what is the common link between these sites."
So far, Landesman and other researchers have found no visible thread that ties the disparate group of mom-and-pop sites together. With addresses such as dubai.travel-culture.com, operationultimategoal.com and directline-citybreaks.co.uk, the sites are mostly based in the UK, but some also hail from India, Brazil and elsewhere. They don't use the same web host, and while most use web serving software from Apache, the versions vary widely, making it unlikely that attackers are exploiting a vulnerability in that program.
The outbreak coincides with another mass infection in progress that's infected tens of thousands of pages, including those of Boston University, security provider Computer Associates, and agencies from the state of Virginia and the city of Cleveland. It infects websites running Microsoft's Internet Information Server web program and the company's SQL database with links the redirect users to servers in China. The malicious sites then try to install keylogging software and other nasties.
As massive as that infection is, it's responsible for less than one per cent of the malicious traffic that ScanSafe has blocked over the past four days, a small fraction compared with the mystery sites Landesman is tracking.
The sites exhibit other intriguing characteristics. They attempt to infect visitors with a javascript file with a randomly generated name that changes each time a person visits the site. Accessing paddingtoncourt.com, for example, (we don't recommend readers try this) might result in the insertion of a script referencing a file titled xxxxx.js, which is dynamically created at paddingtoncourt.com/xxxxx.js. A different visitor might encounter a file titled yyyyy.js served from paddingtoncourt.com/yyyyy.js.
The constant flux makes it impossible for researchers to access the script responsible for delivering the payload or running Google searches that might provide a more comprehensive list of other sites that might be affected.
The script looks for various vulnerabilities specific to the visiting OS, and when it finds one pulls a .Mov file from the domain dedicated.abac.net. That in turn invokes a file from bds.invitations.fr, which installs a backdoor on end users' machines. Victims are unlikely to know they've been infected because the installation is clear and seamless, and the malware uses few PC resources. At last check, only three of 33 antivirus programs detected the malware, which appears to be a derivitive of the Rbot Trojan.
"This is pretty nasty," Landesman says. "It's a new type of compromise, and a pretty significant one." And so far very little is understood about it.
Below is a more comprehensive (though not exhaustive) list of the sites identified as infected. If you can help shed some much-needed light on these attacks, please leave a comment below or contact your reporter using this link.
hxxp://dubai.travel-culture.com/ hxxp://operationultimategoal.com/ hxxp://www.abdet.com/maps/maps-france.html hxxp://www.ace-cranes.com/ hxxp://www.aprazivel.com.br/ hxxp://www.bellingerfurniture.co.uk/ hxxp://www.bmw-carparts.co.uk/ hxxp://www.careinternational.com/ hxxp://www.directline-citybreaks.co.uk/ hxxp://www.directline-holidays.co.uk/ hxxp://www.directline-skiing.co.uk/ hxxp://www.emtbravo.com/ hxxp://www.flintoak.com/ hxxp://www.gujarat.com/recipes/ hxxp://www.henrykaye.co.uk/Cheap-bridesmaid-dresses-and-flowergirl-dresses hxxp://www.hungatecottages.co.uk/the_cottages.html hxxp://www.inthe80s.com/moviequotes/f.shtml hxxp://www.islandescapeholidays.co.uk/Dubai hxxp://www.london-discount-hotel.com/hotelinfo_id__106 hxxp://www.london-discount-theatre.com/productions hxxp://www.moorgateacoustics.co.uk/ hxxp://www.njaiche.org/main.html hxxp://www.noorcapitaluae.com/ hxxp://www.paddingtoncourt.com/ hxxp://www.panacheshoes.co.uk/ hxxp://www.peshawarjobs.com/ hxxp://www.propertyauctions.co.uk/ hxxp://www.propertyworld.com/_Bermuda hxxp://www.quaife.co.uk/Gallery hxxp://www.reallybored.net/ hxxp://www.sharpindialimited.com/dealer-locator.php hxxp://www.thirlmeremeats.com.au/family.htm hxxp://www.thirlmeremeats.com.au/special.htm hxxp://www.travel-culture.com/airblue/ hxxp://www.vauxallparts.co.uk/ hxxp://www.yournewhome.co.uk/Swan-Hill-Homes-LtdDHS issues REAL ID requirements
Posted On at at 1/14/2008 09:41:00 PM by nullThe U.S. Department of Homeland Security mandated controversial changes to state-issued drivers licenses on Friday to reduce forgery and ostensibly increase the security of the identification documents.
The regulations, which are required by the REAL ID Act of 2005, force states to add additional security features to drivers' licenses, check each individual's proof of citizenship, and institute security standards at the offices that issue the identification cards. States that do not comply with the standards by the end of 2009 run the risk that their citizens will not be allowed in federal buildings, on airplanes, and in sensitive government-regulated facilities.
"Americans understand today that the 9/11 hijackers obtained 30 drivers licenses and ID’s, and used 364 aliases," Homeland Security Secretary Michael Chertoff said in a statement announcing the regulations. "For an extra $8 per license, REAL ID will give law enforcement and security officials a powerful advantage against falsified documents, and it will bring some peace of mind to citizens wanting to protect their identity from theft by a criminal or illegal alien."
While the DHS argued that the changes are necessary to prevent future terrorist attacks within the United States, civil-rights advocates have criticized the changes, arguing that REAL ID establishes a national identity card that could threaten the privacy of U.S. citizens. Some security experts have also argued that identity-based security does not eliminate the risks from terrorism.
The REAL ID Act dramatically increases the cost of identification cards, 17 states have passed resolutions rejecting the federal legislation. The DHS argued that the final regulations released on Friday reduce the cost of implementing the changes from $14.6 billion to $3.9 billion.
