Talking malware with Eugene Kaspersky
Posted On Saturday, December 8, 2007 at at 12/08/2007 04:57:00 AM by null
MOSCOW — Amidst growing chatter that the anti-virus/anti-spyware market is gasping for air, a veteran virus fighter says desktop security products must add new protection mechanisms to keep pace with aggressive online criminals.
Eugene Kaspersky, founder/CEO of 10-year-old Kaspersky Lab, says next-generation anti-malware products will have to combine whitelist/blacklist approaches with HIPS (host intrusion prevention system), sandboxing and virtualization to provide what he calls “hybrid protection” for desktops.
“The perimeter is slowly disappearing,” Kaspersky said during a presentation to a group of international journalists here. “It’s getting more and more difficult for reactive [security] technologies to handle the current threats. The world is getting more and more mobile with notebooks, smart phones and Wi-Fi everywhere. We have to develop special products to deal with this new world,” he added.
[ SEE: The anti-spyware market that never existed is officially dead ]
The new protection approaches — already being built into in security suites from Kaspersky Lab, Microsoft (with OneCare) and Symantec (with Norton 360) — will maintain the signature-based blacklist/whitelist capabilities and the behavior-based heuristic analyzers but, in future versions, Kaspersky sees HIPS and sandboxing playing major roles in keeping untrusted software at bay.
With HIPS, sandboxing and virtualization, Kaspersky touted an “open space security” concept that can be combined with vulnerability management capabilities. “We have to build advanced techniques to find and stop new threats… things like rootkit detection, self-protection methods, deep security analyzers,” he added.
During his talk, Kaspersky looked back at the last ten years of fighting malware — from the first file infectors and macro viruses in the 1980s through the network worms in the 1990s to the current crimeware era of for-profit spam/botnet rings.
“At least five malware samples emerge every two minutes,” he declared, pointing out that malware authors are now automating the creation of malicious executables, participating in underground vulnerability brokering and using all kinds of techniques to evade security software.
[ SEE: Kaspersky Lab eyes IPO, acquisitions ]
Kaspersky said the main malware distribution techniques have gradually changed to maximize the use of infected Web pages (drive-by downloads) and pre-infected zombie networks (Trojan downloaders), zero-day exploits and clever social engineering via spam and Web forums.
“It is impossible to point to any one ‘main’ behavior [of malware],” he said. For instance, password stealers now have keylogging functionalities and Trojan downloaders can also be used to send spam and act as botnet clients.
“Modern malware is easy to do and very profitable. They can fight against anti-malware products, hide from anti-virus scanners and even update themselves automatically,” he said.
To fight back effectively, Kaspersky said the new wave of all-in-one solutions must replace the existing approach to fighting viruses.
Hackers targeting 'forgotten' web apps
Posted On at at 12/08/2007 04:57:00 AM by nullSecurity firm Finjan has warned of zero-day attacks targeting popular web apps like media players and chat programs.
The attacks are focusing on popular applications which are usually left unpatched or untracked by administrators.
While most enterprises schedule Microsoft security deployments, applications from other vendors are usually left unpatched and are becoming as an easy target for hackers, according to Finjan.
"The 2007 Sans Institute annual review of the top 20 IT security risks confirms our reports last year, notably in the field of web 2.0 application vulnerabilities," said Yuval Ben-Itzhak, chief technology officer at Finjan.
"There has been a significant move into custom web applications by a growing number of organisations, and it is these applications that criminal hackers are now targeting."
The problem with hackers targeting media players, chat applications, content management systems and discussion forums is that the threats are not tracked on general vulnerability reporting services such as BugTraq and @Risk.
"This makes the task of identifying and protecting against these types of attacks all the more difficult," Ben-Itzhak added.
Finjan agreed with the broad findings of the Sans Institute's analysis of web browser vulnerabilities, but warned that hackers are also focusing on non-Microsoft products.
"The trend towards companies of all sizes adopting open source and, of course, Mac applications, has been steadily increasing over the last 12 months, " said Ben-Itzhak.
"Since most vulnerability reporting services tend to focus on Microsoft software, this makes the business of criminal hackers a lot easier."
Learn how to become a hacker!
Posted On at at 12/08/2007 04:56:00 AM by null PUNE: Want to see a network-attached bread toaster gaining control of a computer? Or, learn how to wiretap an internet telephone call? Then, Pune is the place to be on December 9. For those who think of hacking as malicious attack on computers, this could come as a shock. But for those self-professed hackers who understand the term as an exercise in playfulness, cleverness and exploration, here is welcome news.
India’s hackers are going to come together and discuss their pastime at a day-long convention in Maharashtra’s technology hub this Sunday. Corporate leaders have been invited and cops will be there too, just in case.
“Not all hackers are out there to harm the society. There are many of them who are doing excellent work in their domains and we feel that a hacker should be judged only by his skill, intention and willingness to share his knowledge,” Rohit Srivastava, convenor of Clubhack 2007, said.
The media world over may have focused on the criminals among hackers, but the act itself is not aimed at crime. Richard Stallman, the global guru of free software movement, once roughly defined hacking as exploring the limits of what is possible and crossing it.
Mr Srivastava told ET that for the first time the country’s hackers would come together during the forthcoming event for a serious chat on their role in creating awareness about computer security and freedom. “For some reasons, hacking has been associated with negative connotation all over the world. So, hackers never came in front of the public and worked in closed groups,” he said.
Now, he hopes, Clubhack will give them an annual platform to express themselves. The day-long convention, expected to receive 200 hackers, will have 13 speakers giving various insights on hacking. “The lectures at the convention are divided into three parts — proactive, hactive and reactive — focusing on learning to be safe, learning to hack and learning to investigate. We are targeting the security professionals, CTOs, CIOs, cyber lawyers and law enforcement professionals,” Mr Srivastava said.
Fun sessions would include, in addition to the toaster and internet phone-tapper, a bluetooth peeping session and demonstration of a vulnerability in Firefox browser, which enables an hacker to get password and credit card details of a surfer.
“Any appliance controlled by a microprocessor is susceptible to a hacking attack. This includes the in-vogue intelligent homes, which is very easy for a hacker to break into. For example, a hacker can break into the video peephole system, and make it play an video of a person other than the one standing at the door. Such attacks, though unknown in India, have been executed in some parts of the world, and we need to be informed and armed against them,” Mr Srivastava said.
Other topics include Analysis of Adversarial Code, Backdoor 2.0, Mining Digital Evidence in Microsoft Windows, automated web application testing, Best Cases in Indian IT Act, Subtle Security flaws, Hacking Web 2.0 and vulnerabilities in VoIP products and services.
Data centre looted in multimillion pound overnight heist
Posted On at at 12/08/2007 04:55:00 AM by nullUpdated Reports are emerging of a massive heist overnight at a data centre in London's King's Cross.
According to our sources, the data centre is operated by Verizon Business. A spokeswoman for the firm said it had suffered a "service interruption" last night. She refused to provide any more information on the robbery, saying that it would be "inappropriate" to provide details of what equipment could appear on the black market.
A Reg reader who works for an investment bank says it is suffering major network outages today as a result of the raid. It's thought no data was taken by the robbers, however.
The Metropolitan Police press bureau said it is unable to comment on the news yet. Forensic teams are on site now, it's claimed.
One of the customers of the data centre is the bank JP Morgan, which declined to comment. Its operations have not been affected.
The financial site Here is the City reports that about £2m of gear was lifted. It writes that men dressed as police officers handcuffed staff at the site.
We'll have details from the police as soon as they're released. Do you know more? You know what to do. ®
Hackers Launch Cyberattack on Federal Labs
Posted On at at 12/08/2007 04:54:00 AM by nullInvestigators Believe Chinese Hackers Carried Out 'Sophisticated' Hit
A "sophisticated cyberattack" has been detected at Oak Ridge National Laboratory over the last several weeks, and authorities suspect the hackers are based in China.
The breach might have compromised the personal information of thousands of visitors to the lab, according to a communiqué sent to employees.
The intrusion is under active investigation by multiple agencies. FBI and Department of Homeland Security officials tell ABC News they believe the attacks originated in China with Chinese entities probing U.S. systems.
Investigators have not been able to determine whether the attacks came from government or private entities in China.
The statement, from Laboratory Director Thom Mason, said the attack "appears to be part of a coordinated attempt to gain access to computer networks at numerous laboratories and other institutions across the country."
Other federal labs, including Los Alamos National Laboratory in New Mexico and California's Lawrence Livermore National Laboratory, have been targeted in the scheme, though officials say it is unclear what information might have been compromised at other locations.
Livermore lab spokesman Stephen Wampler tells ABC News that the facilities employees received "approximately 1,000 spam-type e-mails with attachments" in October and November, but said the lab's cybersecurity systems thwarted the attempted attack.
"As a result, there was no compromise of data at our laboratory," he said.
As for the Oak Ridge breach, the message went on to explain that "hackers potentially succeeded in gaining access to one of the laboratory's nonclassified databases that contained personal information of visitors to the laboratory between 1990 and 2004."
The personal information at risk includes names, dates of birth and Social Security numbers of the visitors.
As part of the hit, "thieves made approximately 1,100 attempts to steal data with a very sophisticated strategy that involved sending staff a total of seven 'phishing' e-mails, all of which at first glance appeared legitimate."
One of the fake e-mails appeared to be an announcement for a scientific conference; the other claimed it was a notice of a complaint on behalf of the Federal Trade Commission.
The lab's investigation found that approximately 11 employees took the bait and opened the e-mail attachments, "which enabled the hackers to infiltrate the system and remove data."
The sensitive Tennessee nuclear research facility has a staff of more than 4,200 and hosts approximately 3,000 guest researchers each year.
Glider Emblem the Universal Hacker Emblem
Posted On at at 12/08/2007 01:01:00 AM by null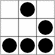
What is the emblem?
The graphic at the top of the page is called a glider. It's a pattern from a mathematical simulation called the Game of Life. In this simulation, very simple rules about the behavior of dots on a grid give rise to wonderfully complex emergent phenomena. The glider is the simplest Life pattern that moves, and the most instantly recognizable of all Life patterns.
Why have an emblem at all?
To some hackers, having an emblem might smack too much of groupthink. But the hacker community is, in fact, a community, knit together by trust bonds over the Internet. One thing we've learned since 1991 is that visible emblems of community are just as valuable to hackers as they are to other kind of human beings. They help us recognize each other, help us affirm common values and cooperate more closely. They're useful social engineering.
Using this emblem means something a little different from just presenting yourself as a Linux fan, or a Perl-monger, or a member of any of the hacker subtribes that have become so successful since the mid-1990s. These are relatively recent developments in a tradition that goes back decades. Back to the homewbrew microcomputer experimenters of the early 1970s; the earliest Unix developers and ARPANET engineers in 1969; and to the SPACEWAR hackers at MIT in 1961.
The hackers, in the broadest sense, are the people who built the Internet, and Unix, and the World Wide Web; our dreams of freedom have changed the world everybody lives in. See How To Become A Hacker for an in-depth look at what that means. If you find yourself nodding in agreement as you read that document, you are one of the people who should be using this emblem.
Why this emblem?
The glider is an appropriate emblem on many levels. Start with history: the Game of Life was first publicly described in Scientific American in 1970. It was born at almost the same time as the Internet and Unix. It has fascinated hackers ever since.
In the Game of Life, simple rules of cooperation with what's nearby lead to unexpected, even startling complexities that you could not have predicted from the rules (emergent phenomena). This is a neat parallel to the way that startling and unexpected phenomena like open-source development emerge in the hacker community.
The glider fulfils the criteria for a good logo. It's simple, bold, hard to mistake for anything else, and easy to print on a mug or T-shirt. It could be varied, combined with other emblems, or modified and infinitely repeated for use as a background.
But what if the wrong people start using it?
A lot of people think this emblem will become worse than useless because script kiddies, crackers and wannabes will be the predominant ones to use it. Yes, that is a risk — but other emblems, like the peace sign or the A-for-anarchy, that have similar risks have retained a lot of utility. If it helps, I've gotten a lot of email from people picking up on it that I know to be hard-core hackers, and I've seen almost no abuse of it.
Will you carry my slightly different idea for an emblem?
Probably not. Part of the point of an emblem like this is instant recognizability. That goal is compromised if there is a lot of variation among the instances. The two most common suggestions are to remove the grid or change the orientation of the glider. Perhaps these variants might have been better, or there is some other idea that would have been superior, but the benefit of having one emblem means it would be a bad idea to switch now that this one has a following. I will carry only images in which the plain-vanilla graphic at the top of this page is clearly recognizable.
Why from you?
Because I maintain the How To Become A Hacker document, A Brief History of Hackerdom, the Jargon File, and am more or less the hackers' resident historian/anthropologist. It's my job to think of these things, if it's anybody's.
The Linux folks have their penguin and the BSDers their daemon. Perl's got a camel, FSF fans have their gnu and OSI's got an open-source logo. What we haven't had, historically, is an emblem that represents the entire hacker community of which all these groups are parts. This is a proposal that we adopt one — the glider pattern from the Game of Life.
About half the hackers this idea was alpha-tested on instantaneously said "Wow! Cool!" without needing any further explanation. If you don't know what a glider is, or why it would make a good emblem, or if you're dubious about having an emblem at all, read the FAQs page.
I first proposed this emblem in October 2003. It has since entered fairly widespread use, as you can see by the number of international translations over on the left. Not universal, because many hackers object on principle to the idea of having an emblem at all, but it appears to be a successful meme.
What will I be saying if I display it?
When you put the glider emblem on your web page, or wear it on clothing, or display it in some other way, you are visibly associating yourself with the hacker culture. This is not quite the same thing as claiming to be a hacker yourself — that is a title of honor that generally has to be conferred by others rather than self-assumed. But by using this emblem, you express sympathy with hackers' goals, hackers' values, and the hacker way of living. See the FAQs page for further discussion.
Yes, as of a mere four days after this proposal was floated, there are mugs and T-shirts. Please note that I had nothing to do with this and I'm not getting a cut; in fact, proceeds are going to the Electronic Frontier Foundation. Now there's a second source with different designs.
Who should not use this emblem?
If you think hacking is about breaking into other peoples' computers, those of us the emblem was invented for do not want you displaying it. Go invent your own emblem, cracker. We'll find some way to shame and reject you publicly if you mess with ours.
I used to have a prohibition against commercial use here. A number of people have argued convincingly that this is impractical and perhaps unfair. But keep it tasteful, or you will be flamed.
How can I use it?
The glider is not copyrighted or trademarked. The recommended way to use it is on a web page, with an image and a link back to either this page or direct to How To Become A Hacker. Here is a snippet of XHTML you can paste into a page.


.O.
..O
OOO
|_|0|_|
|_|_|0|
|0|0|0|
Domain-name issue could aid eavesdroppers
Posted On Friday, December 7, 2007 at at 12/07/2007 06:10:00 AM by null Microsoft warned companies on Monday that a flaw in the way Windows searches for Web proxies could allow an attacker the ability to reroute traffic through a malicious server. The security issues occur when a Windows computer attempts to find a proxy server using Microsoft's Web Proxy Automatic Discovery (WPAD) technology and the organization's domain name starts at the third level or deeper, such as "At this time, we are not aware of attacks attempting to use the reported vulnerability, but we will continue to track this issue," Tim Rains, a spokesman for the Microsoft Security Response Center, said on the teams' blog. "The advisory contains several mitigations that customers can use to help protect themselves from attackers." Successfully exploiting the vulnerability would reroute a Windows computer's Web traffic through the malicious proxy server, allowing man-in-the-middle attacks and eavesdropping. Microsoft has had to deal with a handful of vulnerabilities in recent months caused by the Windows software that handles domain names. In April, the software giant closed a buffer overflow in the remote procedure call functionality of its Domain Name Server for Windows 2000 and Windows 2003. The company is also one of the browser makers searching for a solution to the issue of DNS rebinding, which could be used by an attacker to gain access to resources on a Web surfer's network. Because international domain names frequently assign both the top-level domain and the second-level domain, such as somecompany.co.jp, the software giant stated in an advisory. The WPAD search first attempts to find the server using the fully-qualified domain name (FQDN), and if it doesn't find the server will try the next higher level of the domain name. For example, a search for a proxy server in somecompany.co.jp will look for servername.somecompany.co.jp and then move on to servername.co.jp, which could be a malicious server outside the company's network.co.jp, to segments of users, the vulnerability primarily threatens non-U.S. organizations. Microsoft acknowledged white-hat hacker Beau Butler, who presented details of the issue at Kiwicon in New Zealand last month.
UK cyber-police facing job cuts
Posted On at at 12/07/2007 06:09:00 AM by nullThe UK's Serious Organised Crime Agency (Soca) is expected to lose around 400 staff when the Home Office announces its policing budget later this week.
Many of job losses are likely to be in IT research, according to press reports.
Ian Brown, a cyber-espionage expert at the University of Oxford, told The Times that UK businesses are "more vulnerable than they need to be" following the merger of Soca with the National High Tech Crime Unit last year.
"It is apparent now to many people that the merger was a mistake," he said.
Soca now has overall responsibility for online criminal investigations in the UK. While it has had some success, there are increasing concerns that it has taken on too much responsibility.
An online petition on the 10 Downing Street website has called for the setting up of a single police unit to deal with online crime. It has already been signed by over 100 leaders in the IT field.
Phone phreaks spoof LSD-induced multiple homicide
Posted On at at 12/07/2007 06:09:00 AM by nullThree more individuals have admitted they participated in a series of phone phreak hoaxes that prompted raids by armed special weapons and tactic police teams on the homes of unsuspecting victims.
Jason Trowbridge, of Louisiana and Texas, and Chad Ward of Texas pleaded guilty to multiple felonies, including conspiracy, access device fraud and unauthorized access of a protected computer. Each faces maximum penalties of five years in prison, fines of $250,000 and costs for restitution.
As previously reported, Stuart Rosoff also pleaded guilty to charges in connection with the pranks, which over a course of almost five years snared more than 100 victims and resulted in as much as $250,000 in losses, according to court documents. Angela Roberson, who was charged alongside the trio, also entered a guilty plea but court documents did not elaborate.
A sentencing hearing for Trowbridge is scheduled for late February. Hearings for Ward and Roberson are scheduled for mid March.
Swatters, as the malicious pranksters are referred to, use a combination of social engineering, phone phreaking prowess and computer hacking to spoof the phone numbers of individuals they want to harass. They then make emergency calls to police departments and report crimes in progress, in many cases prompting a response from SWAT teams who conduct emergency raids on the homes of people whose numbers were spoofed.
In many cases, the victims were fellow participants in telephone party lines, which largely act as the phone equivalent of internet relay chat groups. Trowbridge, who went by the names "Jason from California" and "John from California," furthered the scheme by mining personal information about the victims from a host of sources, including consumer reporting agencies, pizza delivery records and newspaper subscription records, according to court documents signed by the defendant.
The personal information Trowbridge provided allowed the gang to make fake emergency calls that had the ring of authenticity. In one case, they posed as an Alvarado, Texas man whose daughter was a party line participant. They told a police dispatcher that he had shot and killed members of his family and was armed with an AK47 machine gun. The caller, who claimed to be high on hallucinogenic drugs, then threatened to kill his remaining hostages unless he was given $50,000 and safe passage out of the country.
Police responded by sending police to the residence of the real man.
In September of last year, Ward himself was swatted by members of the gang. But just a month later, as he admitted in court documents filed last month, he offered money to anyone who would carry out a Swat attack on the Alvarado family. Ward, who went by the name "Dark Angel," also confessed to obtaining personal information on victims by socially engineering telephone company employees.
The documents provide other colorful details. Among them, Rosoff threatened to have the phone service of a Cheboygan, Michigan woman disconnected unless she agreed to provide him with phone sex. When she refused, Rosoff used social engineering to terminate her phone service. He also made false reports to police claiming the woman's children were being abused and discussed ways of having her falsely arrested.
During the course of the conspiracy - which lasted from late 2002 to June of this year and involved as many as 20 individuals - the participants also initiated calls to employers, landlords, families and friends of party line members they held a grudge against. Some of the members who refused to stop using the line found their friends and families swatted.
The case was investigated by the FBI field office in Dallas and prosecuted the the US Attorney's Office for the Northern District of Texas.®
AIM Hack Shows AOL Hasn't Patched Critical Security Hole
Posted On at at 12/07/2007 06:08:00 AM by nullVirginia-based AOL quietly issued a security fix to its AIM instant messaging system this week, after a security researcher demonstrated for Wired News that the company had failed to properly close a September security hole allowing hackers to gain complete control of any PC running the latest version of AIM.
"It could take over 60,000 computers in two days, but I don't want to," says 31-year-old programmer Michael Evanchik, who developed the new attack. "It's a pretty big hole. You don't even have to click anything."
The hack highlights a key difficulty for AOL as it attempts to compete with sites like Facebook and MySpace that feature their own instant messaging systems. AOL has responded by turning its popular AIM client into a multimedia portal, adding extra features that make it easier for hackers to attack the downloadable software.
In October, the company released AIM 6.5 partially to fix a critical vulnerability in how the software handles HTML code. But security experts criticized AOL at the time for rushing out a half-baked solution, and relying heavily on server-side filtering to try and prevent malicious code from traveling through AOL's network. Securing the client from this class of attack could require sacrificing some multimedia functionality.
Monday night's silent server-level patch demonstrates that those experts were right: The AIM 6.5 client remains vulnerable to the same fundamental weakness, potentially allowing malicious hackers to create a worm that infects thousands of users in a matter of hours.
"Instead of locking down the AIM client, they add filters in the server," says Aviv Raff, the security researcher who reported the original remote exploit in September, and who analyzed the newest attack for Wired News. "Filtering in the server will never be enough. It's like a cat and mouse game."
Raff said that as soon as AOL told him they fixed his September exploit, he quickly developed functioning variants himself -- an easy process since the company was essentially filtering by keywords.
AOL spokeswoman Erin Gifford , however, says all is well.
"We have taken steps to protect users from this known and reported issue," said Gifford, after Wired News reported the issue.
Evanchik said he was moved to develop the attack after an anonymous MySpace user began harassing his sister. He planned to use it to deliver a homemade key logger to the user's machine, though he says he hasn't done so.
His attack was a single line of JavaScript that performed two functions. First, it set up an error handler that would download and run a malicious file from the internet. Then it directed the AIM client to try and display a non-existent image from the web. Because the image link was broken, AIM 6.5 followed the error instructions and turned over the victim's computer to the attack.
AOL's response was to add Evanchik's specific attack string to the company's server-side filtering software. AOL says that's good enough, and it doesn't expect to see any more exploits.
Information chief warns of further data loss
Posted On at at 12/07/2007 06:08:00 AM by nullInformation Commissioner Richard Thomas has warned that the UK is not out of the woods when it comes to damaging data loss incidents.
Several other public bodies have admitted to losing data following the crisis at HM Revenue & Customs when unencrypted discs containing details on 25 million UK residents on the child benefit database were lost in the post.
"A number of public and private sector organisations have come to us saying that they think they have found a problem," Thomas told the Commons Justice Committee. "I think there is certainly more to come out in the wash."
Thomas declined to name any of the parties involved, but confirmed that they had approached the government on a "confessional basis".
HMRC today announced a £20,000 reward for the return of its missing CDs. Police have searched for leads on possible routes between HMRC and the National Audit Office, including rubbish dumps.
Police have also appealed for HMRC and National Audit Office staff to keep their eyes peeled in case the package has since been delivered.
IT pro admits stealing 8.4M consumer records
Posted On Wednesday, December 5, 2007 at at 12/05/2007 05:56:00 AM by nullA senior database administrator for a consumer reporting agency in Florida has admitted stealing more than 8.4 million account records and selling them to a data broker. He netted $580,000 over five years from the scheme.
William Gary Sullivan, a DBA for Fidelity National Information Services, faces up to 10 years in federal prison and $500,000 in fines, although prosecutors agreed to recommend a more lenient sentence in exchange for his guilty plea. He's also required to surrender all remaining proceeds and pay restitution to his victims.
Working for a subsidiary called Certegy Check Services, Sullivan used his access to Fidelity's database to pilfer records that included individuals' names, addresses and financial account information, according to court documents. To cover his tracks, he incorporated a business called S&S Computer Services, which sold the data to an un-indicted accomplice. According to authorities, this unidentified person resold the information to direct marketers, including one called Strategia Marketing, which also went by the name Suntasia.
The scheme came to light in July, when Fidelity disclosed that an employee absconded with 2.3 million records. Fidelity was alerted to the theft by a retail customer, who noticed a "correlation between a small number of check transactions and the receipt by the retailer's customers of direct telephone solicitations and mailed marketing materials".
Fidelity later raised the estimate to 8.5 million records. The company is unaware of any identity theft or fraudulent financial activity resulting from the theft. Rather, it believes the stolen records were used for marketing purposes.PC Tweaks for Silkroad
Posted On at at 12/05/2007 05:40:00 AM by nullWindows Vista
Combination of factors.
- Install DirectX 9.0C from Microsoft.
- Right click on the Silkroad shortcut. Click on Properties, then go to the Compatibility tab. Make sure that Silkroad is set to run in Windows XP SP2compatibility mode.
- Update all your drivers.
- Reboot.
- Right click My Computer, then click on Properties. Go to Advanced, then Settings, then Data Execution Prevention. Ensure that Silkroad is an exception or that DEP is only turned on for essential Windows Programs and Services.
- Right click Silkroad, then click on "Run as administrator."
*In addition, many drivers will have specific installation steps andinstructions. Ensure that you follow them.
How can I check whether my computer is secureand cannot be hacked?
Go to thispage on grc.com, click proceed, then click "All Service Ports."The best result is every single box showing green. If any are blue, you're OK.You need to ensure, however, that none show up as red. If they do, you shouldinstall a firewall, activate XP's built-in firewall, or activate the firewall atyour router or modem.
How can I check whether my password is a goodone?
Enter a password similar to your real password to thisutility on Microsoft's website. Ensure that Javascript is enabled.
How do I update my graphics card driver/findout what my graphics card is?
Confusion.
- Go to Start, then click on Run. Type in dxdiag and hitenter.
- Click on the Display tab. The name of your card will be under the section labeled "Device".
- To update the driver, go to the website of the card manufacturer. (Example 1: NVIDIA MX/MX 400. Manufacturer is NVIDIA, thus www.nvidia.com. Example 2: ATI Radeon 9000. Manufacturer is ATI (Note: Merged with AMD), thus ati.amd.com)
Bad download.
Download it again. Make sure you're using InternetExplorer with no download managers or accelerators.
Server Undergoing Inspection when Silkroad isonline/Cannot access Silkroad website/........(9)/C9/"Silkroad.exe has encountered a problem andneeds to be closed. We are sorry for the inconvenience.":
Internet connection to Silkroad blocked.
- Use Notepad to navigate toC:\Windows\System32\drivers\etc and open the file labeled hosts.
- Delete everything in the file (Ctrl+A, Delete). Replace it with:
127.0.0.1 localhost
121.128.133.26 gwgt1.joymax.co.kr
121.128.133.26 gwgt1.joymax.com
121.128.133.27 gwgt2.joymax.co.kr121.128.133.27 gwgt2.joymax.com
64.152.34.142 joymaxnpro.nefficient.com
121.128.133.12 silkroadonline.net - Save it and reboot.
- Ensure that Silkroad is allowedthrough all firewalls including software and hardware (allow port 15779 TCP).
- Click Start, then go to Run and type wscui.cpl. Hit OK. Click "Windows Firewall."
- Go to the tab labeled Exceptions, and then click on Add Program.
- Go to C:\Program Files\Silkroad, and add both silkroad.exe and sro_client.exe.
After that, right click on My Computer, then go toProperties. Go to Advanced, then Settings, then Data Execution Prevention.Ensure that Silkroad is an exception or that DEP is only turned on for essentialWindows Programs and Services.
Finally, if none of the previous have solved your issue, reboot and tap F8 as the system is starting.Select "Safe Mode with Networking." Update Silkroad, then reboot back into normalWindows.
Website is not loading correctly/Cannot registerdue to website design issues.
Internet browser is not rendering page properly.
- Go to Microsoft Update and install any availablepatches, then reboot.
- Use Internet Explorer to access the Silkroad Online website.
Someone else has already registered from yourinternet address.Register at your public library, your workplace, oryour school.
Alternatively, use a proxy. Sites include projectbypass.com, stupidcensorship.com, orvolleyballwizard.com. http://proxy.org/cgi_proxies.shtmloffers a list of many more. You simply navigate to these websites, then in thebox tell them to go to the Silkroad Online website. Note that many proxies arevery slow, you will need to wait for them.
????? Error:
Driver issue(s).
- Update all drivers including sound and graphics.
- Update DirectX to 9.0c.
- Download any updates from MicrosoftUpdate.
- Check to make sure that your Windows resolution setting matchesyour Silkroad in-game resolution settings.
*In addition, many drivers will have specific installation steps andinstructions. Ensure that you follow them.
Random reboots:
System is configured to automatically rebootupon system failure.
- Right click My Computer, then go to Properties.
- Go to the Advanced tab, and under Startup and Recovery click Settings.
- Uncheck Automatically Restart, then hit OK.
Driver issues.
Update all drivers.
*To find the specific drivers needed for your system, go to the website ofyour motherboard manufacturer or the website of the OEM (Original EquipmentManufacturer: Dell, Compaq, Gateway, Lenovo, etc) and then find the"Downloads" section. Select your make/model/version, then you can finda list of driver that you need as well as a download link. You are not yet donehowever, as these drivers are probably out of date. Next, you need to take thename of driver (such as "SiS Accelerated AGP"), and google for thecompany name (Example: SiS). After finding the company website, you need todownload the specific driver ("Accelerated AGP"). You will need torepeat this process for every single driver.
*In addition, many drivers will have specific installation steps andinstructions. Ensure that you follow them.Game Hack Detected/Virus Detected in Silkroad:
GameGuard has detected a game hack or yourantivirus program has detected a virus.
- Close all running programs in the background. Ensure that you are not using any hacks including a modified client.
- Reboot.
- Update your antivirus program.
- Scan your entire disk for viruses.
Outdated C++ libraries and/or outdated drivers.
- Download VC6RedistSetup_Enu.exe.
- Agree to the license agreement, and extract the results to C:/.
- Go to C:/,and run vcredist.exe.
- Update all drivers including sound and graphics.
- Also update DirectX to 9.0C and go to Microsoft Update.
*In addition, many drivers will have specific installation steps andinstructions. Ensure that you follow them.
"Replacer.exe is corrupt":
Corrupt file
- Go to C:\Program Files\Silkroad.
- Rename replacer.exe to replacerbackup.exe
- Replace replacer.exe with this.
Your computer is infected with spyware/adware.
- Download Hijackthis 1.99.1 from Merijn.
- Extract HijackThis.exe to C:/Hijackthis.
- Run HijackThis.exe, and click "Do a systemscan and save a logfile."
- When it's done, a notepad window will popup. Copy everything.
- Go to a reputable forum like castlecops.com and postthe log in the section for HijackThis logs.
guide how to unlock your iphone
Posted On at at 12/05/2007 02:55:00 AM by nullguide how to unlock your iphone.
Things needed:You will need an iPhone (Jailbreaked +SSH enabled + Installed Binkit)And 2 needles (to conduct the electricity) or use your imagination
And all the needed files - Files Needed
First Set Of Instructions- Install winscp (get it here Winscp)
- Extract Putty from the rar then put is somewhere on the desktop.
- Install the hexedit from the folder Hexedit. (this was included in these files)
- Make sure the binkit is on your iPhone. (if not it’s included in the rar)
- Copy the files in the bin folder in rar to your iphone in the /bin folder
Now its time to open your iPhone (Use anything you can think of that would not scratch it a guitar pick is good but I used a knife which made a few scratches, but if you want to I am sure you will find something that wont scratch)
This Guide is a great guide on how to open your iPhone!
- Now open up the metal case right below the battery.
- Now Startup your iphone (plug it into your computer)
- Connect your iPhone to your wifi network, and set up a connection from your pc to the iphone with winscp.
If you don’t know how:
- open WINSCP
- Select new.
TO GET YOUR IP OF YOUR IPHONE SIMPLY LOOK AT YOUR IPHONE CLICK ON SETTINGS GOTO Wi-FI; THEN UNDER YOUR CHOSEN NETWORK Click the little Blue Arrow
This should Show your IP ADDRESS Under IP Address!
Now! Lets get started
- Enter the ip of your iphone into the host address field - username : root
- password : dottie
- File Protocol SCP
- save the settings and login
( just ignore the errors ;-))
- Create a new folder “etc” in the folder /usr/local/etc or /etc
- Copy termcap from rar to this folder.
- Copy bbupdater from rar to /bin
- Goto the folder /system/library/launchdeamons and move the file commcenter.plist to your desktop (make
sure the file is moved and not copied. reboot the phone. (you can use putty to do this )
- start putty
- enter the ipaddress of your iphone in the hostname field, and click open.
- login with username : root and the pass : dottie
- type reboot
- disconnect and reconnect the phone. (it will automaticaly turn on)
- Start putty again and login.
- type : minicom -s
- select serial port setup and type : A.
- enter: /dev/tty.baseband Enter
- press esc
- select save setup as dfl
- when entering minicom type AT
- the modem should respond. OK
This is where you will touch your two points together using your needles! Only without soldering!

Or a clearer picture for those who are unsure !

The two points should be touching
There should not be any response… even wen you touch the needles again.
- Make sure the needles are not touching now.
- exit Minicom (CTRL A then X)
- type : bbupdater -v
- type minicom it should respond ok when entering the AT command.
- when this is the case. The needles where connected right ![]()
Now time for more things! If you got this far WELL DONE!
Now…….. The rest NORDumper is located in the files you downloaded earlier!
- Copy the files from folder NORDumper from the rar to /usr/bin on your iphone using winscp
- in putty, go to this folder. type : cd /usr/bin type : ls you should see the nordumper file
- type : NORDumper dump.bin (this is case sensitive…)
- now you have to wait for about 10 to 20 mins. Wait till the dump is completed.
Now for the next step!
- Copy the contents of the folder ieraser from the rar also to /usr/bin on your iphone using winscp.
- Start Cygnus Hex Editor. and open the file ICE03.14.08_G.fls. (included in the rar) (only for firmware 1.0.1 and 1.0.2 !!!!)
- Select the range from 000001A4-000009a4. In the taskbar the selection should show 1A4-9A4. (verry important !!)
- then goto menu edit–> select copy to file. name the file : secpack
- Upload this file to /usr/bin on the iphone.
- in putty type ieraser. (if it hangs try http://lpahome.com/ieraser.rar )
Next Step
- copy the dump.bin from /usr/bin to your PC using winscp.
- Open this file with Cygnus Hex Editor.
- Select the range 00020000-00304000
- In the taskbar it should show 20000-304000 (if not do the selection again)
- goto menu edit–> select copy to file. name the file : nor
- open this file with the hexeditor.
- Find the row 215148 and change 04 00 A0 E1 to 00 00 A0 E3
- save the file, and upload it to /usr/bin using winscp
Next Step
- copy the files in the folder iunlocker from ther rar to /usr/bin
- Touch YOUR NEEDLES TOGETHER HERE! (Touching where they should)
- with putty goto /usr/bin and type iunlocker
- when the program halts. Remove your needles and press a character on your keyboard followed by Enter.
- you will see a lot of numbers running on your screen. This also takes a while…
- after it’s done type : bbupdater -v
- it should show : xgendata and some more text i can’t remember..
Last Instructions
- start minicom again.
- type AT+CLCK=”PN”,0,”00000000″
- type AT+CLCK=”PN”,2 this should respond in a 0 .
- Congrats !!!! youre phone is now simlockfree.
- now copy back the commcenter.plist file (don’t forget)
WELL DONE!
- Now put your phone back together and insert your chosen simcard
- Turn on the phone
The new simcard will not be accepted yet.
Now activate your IphoneYou could update the phone with itunes to 1.0.2.
After that you could use iactivator to jailbreak and to generete the keys and activate the phone.
IT pro admits stealing 8.4M consumer records
Posted On Tuesday, December 4, 2007 at at 12/04/2007 11:30:00 PM by nullA senior database administrator for a consumer reporting agency in Florida has admitted stealing more than 8.4 million account records and selling them to a data broker. He netted $580,000 over five years from the scheme.
William Gary Sullivan, a DBA for Fidelity National Information Services, faces up to 10 years in federal prison and $500,000 in fines, although prosecutors agreed to recommend a more lenient sentence in exchange for his guilty plea. He's also required to surrender all remaining proceeds and pay restitution to his victims.
Working for a subsidiary called Certegy Check Services, Sullivan used his access to Fidelity's database to pilfer records that included individuals' names, addresses and financial account information, according to court documents. To cover his tracks, he incorporated a business called S&S Computer Services, which sold the data to an un-indicted accomplice. According to authorities, this unidentified person resold the information to direct marketers, including one called Strategia Marketing, which also went by the name Suntasia.
The scheme came to light in July, when Fidelity disclosed that an employee absconded with 2.3 million records. Fidelity was alerted to the theft by a retail customer, who noticed a "correlation between a small number of check transactions and the receipt by the retailer's customers of direct telephone solicitations and mailed marketing materials".
Fidelity later raised the estimate to 8.5 million records. The company is unaware of any identity theft or fraudulent financial activity resulting from the theft. Rather, it believes the stolen records were used for marketing purposes.Microsoft, Mozilla face off over bugs
Posted On at at 12/04/2007 11:28:00 PM by null Microsoft and Mozilla have again locked horns over whose browser is more secure. On Friday, Microsoft posted a report showing that, while the software giant and Mozilla have both improved security in the latest version of their browsers, Internet Explorer has overall had fewer publicly disclosed flaws than Mozilla's Firefox in the past three years. While the report stopped short of calling Microsoft's browser more secure, the analysis spotlighted bug counts as a measure of "security quality." "While the results in this study showing fewer vulnerabilities in Internet Explorer might be surprising to some, to others the results will simply be a confirmation that improving security is a hard job even with the best of intentions," Jeff Jones, security strategy director for Microsoft, said in the report. Mozilla immediately struck back at the critique, pointing out that the open-source browser has done better than Internet Explorer with significantly lower average times to patch a vulnerability. Moreover, Mozilla's vice president of engineering Mike Schroepfer also questioned whether Microsoft public vulnerability disclosures have any relationship to the actual number of flaws found in any of the company's products. "A vivid reminder that there is no way for anyone outside of Microsoft to confirm how many vulnerabilities ever existed in Internet Explorer," he said in a blog post, adding: "Bug counts are meaningless, what matters is whether you are at risk or not." Microsoft and Mozilla have both boasted about the security of their respective browsers. Following the release of Internet Explorer 7 and Firefox 2.0, the two organizations faced off over the browsers' phishing features. In July, the two groups argued over whether the browsers should check uniform resource identifiers (URIs) before passing them to other applications. Mozilla quickly fixed the issue, while Microsoft originally argued that the problem should be handled by third-party application, before ultimately releasing a patch. Ironically, market share may mean far more than the number of exploitable security holes. An survey of attacks against Mozilla Firefox 1.5 and Microsoft Internet Explorer 6 Service Pack 2 found that, while Firefox had more publicly disclosed flaws, every single attack appeared to target Internet Explorer 6 SP2.
Bank details for sale on the web
Posted On at at 12/04/2007 11:28:00 PM by nullMore than 100 websites have been found selling account information for UK bank customers, including account details, Pins and security codes.
UK Information Commissioner Richard Thomas has called for an immediate investigation after The Times claimed that it had been able to download the information for 32 UK customers.
One individual was reportedly willing to sell up to 30,000 British credit card numbers for as little as £1 each.
An Information Commission spokesman said that the details on sale seemed to be for active accounts and could be enough for someone to spend money online.
Brian Spector, general manager at information security company Workshare, warned that the government had to act now.
"As major security breaches make their mark on the UK's consciousness, the true cost of a data breach is being revealed. Millions of people are at risk of fraud as their details are made available online for as little as £1," he said.
"We strongly believe that the government should introduce more stringent data breach laws and prosecute any organisation which takes such a laissez faire approach to protecting customer data."
Spector added that there is no excuse for major data breaches as the technology is available to enforce security policies to prevent leaks from occurring.
"But without punitive measures in place for breaches, organisations will sadly continue to adopt this 'it won't happen to me' attitude," he said.
This latest issue comes hot on the heels of the government's losing 25 million individuals' data, and misplacing two discs with the details of 15,000 Standard Life customers.
EFF wants to saddle you with metered Internet service
Posted On at at 12/04/2007 11:27:00 PM by nullThe EFF (Electronic Frontier Foundation) last week publicly joined Free Press and Public Knowledge in recommending a metered Internet service as the alternative to Comcast’s BitTorrent throttling. The extremist “Net Neutrality” crowd that wants to regulate the Internet with bans on per-user charges/contracts for Enhanced QoS are so busy trying to revive their cause by using the Comcast issue that they’re overlooking the fact that these three groups are trying to bring you a metered Internet service. The media for the most part has missed the boat on what’s really going on and they present this to the public as if EFF is trying to protect the public’s interest from evil corporations.
The EFF goes as far as touting the Australian model for broadband service. Just to be sure this isn’t some kind of mistake, I personally confirmed with EFF this is what they want. In their report they write:
The Australian broadband market offers an illustration of how this can work in practice. The selection of Australian broadband options can be searched at http://bc.whirlpool.net.au/bc-plan.cfm. It includes a wide selection of plans with different peak and off-peak quotas, some with a traffic shaping after a quota has been passed and others with a wide range of per-gigabyte fees. It also includes explicitly “no set limit” plans where the ISP reserves the right to deem certain usage excessive, and more expensive, truly unlimited plans where the user can saturate their link 24/7 if they wish.
I checked out the link and a Cable broadband connection costs $40/month with a 400 MB cap and a $150/GB overage charge. Just imagine if you accidentally left the BitTorrent client on for a weekend or if the kids use Grandma’s computer to download a bunch of videos racking up hundreds of dollars in charges. We’re all going to have to go back to the cell phone model where we worry about peak and off/peak hours and how many megabytes we used just like we worry about how many minutes we use.
Well no thanks EFF, I as an American have no interest in paying higher prices like they do in Australia (no offense to the beautiful country of Australia and its people). Not only does a metered Internet service plan screw the low-end users, it makes BitTorrent or any kind of peer-to-peer networking cost prohibitive. The EFF ironically claims its standing up for BitTorrent rights when it fact it would kill it with metered Internet services.
Mozilla rubbishes IE Firefox security study
Posted On at at 12/04/2007 11:25:00 PM by nullMozilla developers have hit back at a Microsoft study that suggests Internet Explorer is more secure than Firefox.
The study, Internet Explorer and Firefox Vulnerability Analysis, is based on a comparison between the number and severity of security updates issued for IE and Firefox since the release of Firefox in November 2004.
In the three years since then, Microsoft has fixed 87 vulnerabilities in various flavours of IE while Mozilla has patched 199 vulnerabilities in Firefox products.
The report, compiled by Jeff Jones, a security strategy director in Microsoft's Trustworthy Computing group, also found IE scored fewer vulnerabilities than Firefox across all categories of severity.
Mozilla said Microsoft's comparison is, at best, meaningless.
"Just because dentists fix more teeth in America doesn't mean our teeth are worse than in Africa," Mike Shaver, chief evangelist for Mozilla told eWEEK. Shaver took particular exception at Microsoft's decision to equate a large number of bug fixes with insecure software.
"It's something you'd expect from maybe an undergrad," he said. "It's very disappointing to see somebody in a senior security position come out and say that because an organisation is more transparent about their bugs and fixing them, they're somehow less secure."
Shaver added that even taken on its own merits the comparison between IE and Firefox is potentially misleading because Redmond often bundles multiple fixes in a single update, a phenomenon repeated to an even greater extent with the release of service packs.
Mozilla is putting an effort into encouraging users to update to the latest version of its software more quickly alongside greater emphasis on rapidly responding to security problems. Microsoft's efforts to suggest this is a bad thing are out of tune with the rest of the industry, Shaver argues.
"Shouldn't they be trying to fix more bugs, rather than writing reports that would 'punish' them for actively improving the security of their users rather than hoping that defects aren't found by someone who they can't keep quiet?"
"Microsoft should be embarrassed to be associated with this sort of ridiculous 'analysis'. We don't pretend that hiding the rate of fixes improves our users' security in any way, and we never will. We're transparent and aggressive in dealing with security issues, and 130 million Firefox users are safer for it every day," Shaver writes in a blog posting here.
Microsoft's Jones is no stranger to controversy. His previous study - a comparison between the number of security vulnerabilities in Windows Vista, Mac OS X, and Ubuntu Linux in the first six months of availability of the respective OSes - united Mac and Linux fans in opposition to Redmond's contention that Vista was more secure than its rivals
California gov site invaded by smut and malware again
Posted On at at 12/04/2007 12:19:00 AM by nullFeels like the first time
Raising troubling questions about the security of America's government websites, more domains ending in .gov have been found hosting links that push porn and malware.
They include the Marin County Transportation Authority, which has has watched its site get hacked at least twice before. In early October the domain forced the shutdown of all California government websites until admins could remove the links. A week after the sites were disinfected, the rogue pointers returned.
On Friday, more than 24 hours after this post from Sunbelt Software first reported the reemergence of the links, the gov site was riddled with at least a dozen pages that, when clicked, redirected users to smut sites. Users then got a messaging saying they had to install a special codec in order to view the content. The codecs contain Trojans that install malware.
By Friday evening in California, the tainted pages were finally removed, and the executive director of the agency apologized for the problem.
The other site actively pushing smut and malware at the time of writing was USAid, a federally operated agency that extends aid to countries recovering from disasters. Perhaps they should attend to their own affairs first.
Over the past several months, the poisoning of search caches belonging to Google and other search engines has emerged as a chief tactic by miscreants in inflating rankings of their malicious websites. At the moment, Google security pros are scrambling to eradicate a flood of malicious links. Problem is, the purveyors of smut and malware are quickly able to taint the cache with a new batch of domains. The whack-a-mole battle finally prompted Google to issue this request for help from its users.
The infections of the gov sites, which are easily documented by these two Google searches (safe to click if you don't mind "porn" in your url, but you probably shouldn't click on any of search results), appear to be yet another attempt to boost the rankings of the malicious sites.
Dianne Steinhauser, executive director of the Marin County Transportation Authority, said she thought the problem was fixed in mid September, after her agency dumped its old web host, StartLogic, and contracted with a new one.
"Even though we quit any web hosting with them, they had a publicly accessible web page with our name on it," she told The Register. "They still had a web service under our name, and that was a complete surprise."
Hackers were able to create the porn- and malware-infested pages by infiltrating StartLogic's system, she said. The pages became inaccessible after her office directed the web host to remove the web-accessible service, she said.
"I am exceptionally apologetic for anyone that was contaminated by virtue of our name," she said.
Attempts to reach representatives of StartLogic and USAid were not successful.
FBI Arrests Pair Wanted in $7 Million Robbery
Posted On at at 12/04/2007 12:13:00 AM by nullCLEVELAND — A couple wanted in the disappearence of $7 million in cash and checks from an armored car company was arrested on Saturday in West Virginia, the FBI said.
Roger Lee Dillon, 22, and his girlfriend, Nicole N. Boyd, 24, were arrested by agents from Cleveland, Youngstown, Pittsburgh, Pa., and Beckley, W.Va., early Saturday morning outside Beckley, FBI Special Agent Scott Wilson said.
Click here for MyFoxCleveland.com for coverage.
Wilson said "a large sum of money" was recovered at the time of the arrests. Dillon was an employee of AT Systems International. Two drivers discovered the safes had been cleaned out and called police.
Dillon was charged with bank larceny, and Boyd was charged with aiding and abetting, the FBI said. The FBI is holding a news conference on Monday, Wilson said.
A pickup truck belonging to Dillon was found in a parking lot in Salem, Ohio, after a resident recognized it from news reports, police said. The FBI towed the truck on Thursday.
Officials said the alarm system was deactivated, safes were opened and money to be delivered to banks was gone. Then the alarm system was reactivated.
Dillon didn't show up for work Tuesday, the FBI said.
He began work at AT Systems International's Liberty office less than one year ago, said a representative of Garda, the company that purchased AT Systems in April. AT Systems offered a $100,000 reward for information leading to the arrest and conviction of anyone responsible. Wilson said he didn't know if anyone was eligible to receive the reward because of the arrests.
Under half of IT managers using encryption
Posted On at at 12/04/2007 12:12:00 AM by nullA recent survey of public and private UK organisations has revealed that nearly two thirds are not planning to change IT spending priorities in light of the data loss at HM Revenue & Customs.
IT security firm Check Point found that under half have deployed data encryption, and fewer than 40 per cent have any endpoint security deployed on PCs, laptops and mobile devices.
The email survey showed that the majority of respondents believe their company to be secure against data leaks, and just 11 per cent believe that a highly publicised loss of personal data would influence their IT spending priorities.
The research also showed that business PCs, laptops and mobile devices are vulnerable to threats from malware as the majority have no endpoint security to protect against unauthorised access or malware.
Interestingly, 73 per cent of respondents said that their organisation's IT security policy includes data protection guidelines such as the use of USB drives for transporting data.
"It is worrying that a majority of companies feel safe against data loss, yet over half do not have basic security measures in place to stop the type of employee behaviour that caused the leak at HMRC," said Nick Lowe, regional director for Check Point in northern Europe.
"Securing any kind of sensitive data must be automated so that employees cannot alter or stop the security processes.
"Organisations have to protect their data, themselves and their employees against the risk of data leaks, and automation is the only way to do that."
According to the report, 85 per cent of companies strongly agree with mandatory notification of affected parties in the event of a data breach, as is the law in most US states.
Apple QuickTime under siege
Posted On at at 12/04/2007 12:10:00 AM by nullot counting silent (undocumented) fixes, Apple has patched at least 32 security flaws affecting QuickTime in 2007. Last year, the QuickTime patch count was 28. Five were documented in 2005.
Judging by the public release of details — and exploit code — for zero-day flaws affecting the company’s flagship media player, it looks like the number will rise again in 2008.
Take a quick peek at Milw0rm.com, a popular security research site that hosts proof-of-concept exploit code. At the moment, there are four different remote exploits for unpatched QuickTime vulnerabilities.

Lower down the page, there are two more proof-of-concepts for denial-of-service holes. These affect both Windows and Mac OS X users, increasing the likelihood that in-the-wild attacks against unpatched QuickTime holes will soon appear.
[ SEE: Latest QuickTime bug leaves XP, Vista vulnerable ]
The latest zero-day, a stack buffer overflow vulnerability in the way QuickTime handles the RTSP (Real Time Streaming Protocol) Content-Type header, is among the more serious flaws affecting QuickTime this year.
It affects most versions of QuickTime prior to and including 7.3 running on all supported Apple Mac OS X and Microsoft Windows platforms. Since QuickTime is a component of Apple iTunes, iTunes installations are also affected by this vulnerability.
A US-CERT advisory spells out the risks:
An attacker could exploit this vulnerability by convincing a user to access a specially crafted HTML document such as a Web page or e-mail message. The HTML document could use a variety of techniques to cause QuickTime to load a specially crafted RTSP stream. Common Web browsers, including Microsoft Internet Explorer, Mozilla Firefox, and Apple Safari can be used to pass RTSP streams to QuickTime, exploit the vulnerability, and execute arbitrary code.
This vulnerability could allow a remote, unauthenticated attacker to execute arbitrary code or commands and cause a denial-of-service condition.
The sharp rise in QuickTime flaw discoveries has set tongues wagging in security research circles and calls into question Apple’s code review process.
[ SEE: QuickTime high on list of most vulnerable Windows apps ]
“QuickTime is the new IE and Apple is the new Microsoft,” said a researcher who works closely with both companies on vulnerability reports.
Those comparisons aren’t far-fetched. QuickTime, like Internet Explorer, is ubiquitous on Windows and often run in an unpatched state for long periods — on both home and business computers. Apple, like Microsoft, has attracted scorn among some flaw finders for its slow response to serious issues — and publicly documented squabbles with researchers.
Now there are calls for Apple to beef up its anti-exploitation protection mechanisms. Former Gartner analyst Rich Mogull, now an indie consultant at Securosis.com, offers the following advice:
This situation highlights why it’s so important for Apple to finish some of the security improvements they started implementing in Leopard. Both library randomization and sandboxing can help prevent exploits of vulnerabilities like this. If Apple were to add outbound blocking to the application firewall, it would let us block these kinds of attacks without having to know anything about ports and protocols. Apple is clearly on the right path, and I look forward to future updates that will keep me protected even when a new, unpatched vulnerability is in the wild.
Better yet, Apple might want to (gasp!) borrow a page from Microsoft’s playbook and implement an entire SDL (Security Development Lifecycle) process to cut down on flaws and reduce the attack surface when zero-days emerge.
Silkroad Skill Error Status and explaination
Posted On Monday, December 3, 2007 at at 12/03/2007 11:39:00 PM by nullSilkroad Skill Error Status and explaination
Curse Series
Confusion
Confusion refers to the state where you see mixture of objects nearby, and cannot distinguish comrades from enemies. This status error is only affective on monsters, and confused monsters will attack the enemies of the caster.
Disease
Body and mind is weakened due to a curse, and the chance of getting a bad status increases under this state. Impossible to be cured using medicines, and the only way to be cured is through the help of others.
Fear
It is difficult to even look at your enemy, because constant fear arise deep inside your heart. You cannot select or attack the target you fear for a fixed time.
Hidden
Unknown force has gotten inside your body, and you do not know when the force will explode. No one knows when the force will explode, and when it does there will be damage to life power.
Zombie
Refers to the state where your life energy changes to poison due to a curse that temporarily changes your body to a dead state. For a fixed time your HP recovery value will be changed to HP reduction value.
Restriction Series:
Bind
Bind refers to the state where you cannot move because your legs have been binded to the ground. Being attacked by a magical attack will release you from the bind state.
Combustion
Combustion is the state where you cannot concentrate and waste your mind energy on needless things. MP will be wasted for a fixed time, and until you recover from combustion state your MP recovery will be affected.
Division
Division is the state when you have been tempted and your judgment is playing tricks on you. Under division state you are not able to make the right decisions, resulting in decrease in physical and magical defense power.
Dull
Due to the enemy's hypnosis, you think there is a heavy weight on your hands and feet. Movement speed and attack speed will decrease for a fixed time, but it is possible to get out of the dull state with the help of a comrade.
Freezing
Frozen refers to the state where your body has been paralyzed due to extreme cold energy. You cannot move nor use skills for a fixed time.
Frostbite
The cells in your body are nervous and your movement becomes slow due to the cold energy that has gotten into your body. Your movement speed and attack speed will decrease for a fixed time.
Impotent
Due to powerful damage, you have lost all energy and experience hard time trying to move a finger. Under impotent state your physical and magical attack power will decrease.
Panic
Your mind has been damaged, and you do not know what to do. Because of fear and surprise you do not react to others healing, and only receive part of it.
Petrify
Petrify is the state where you are stoned solidly as if you have become one with earth. Under petrify state you cannot do anything, and you will slowly lose life power, resulting in death. In order to get out of petrify state, a comrade must attack me to relieve the body from getting stoned.
Short-sight
The spritual damage from the curse paralyzes the nerves of your eyes, causing you not to be able to see far away distance. The range of long distance attacks will be reduced.
Sleep
Refers to the state where you are in a deep sleep from being hypnotized by the enemy. Under sleep state you cannot do anything, and you can only wake up when you have been damaged.
Stun
Refers to the state where you can't do anything because you have been attacked severely by an enemy. Cannot wake up with your own strength, and can only be cured through the help of others.
Weaken
Weak is the state where stress takes place due to factors hunting your mind. Your magical defense power will decrease until your mind recovers.
Weakening Series
Bleed
Bleed is a state where your wound is getting worse by being cut with a sharp weapon. Life power is constantly being reduced, as well as your physical/magical defense power.
Burn
Constant pain is received due to the fiery fire energy. Until the heat is gone, your life power will decrease for a fixed time.
Darkness
Refers to the state where your vision decreases due to a powerful light that paralyzes the nerves of your eyes. Hit ratio is reduced because you cannot see well with decreased vision.
Decay
Decay state occurs when your skin is weakened by attacks that erode your body. Under decay state your physical defense power decreases, making you vulnerable to outer physical attacks.
Electric Shock
Your body has been shocked by electricity and your body movement has been temporarily slowed down. Until the electricty energy is gone, your parry ratio will be reduced.
Poisoning
Constant pain is received due to the poison. For a fixed time life power will decrease until the poison is cured.


